| Trend Micro Quotes |
| Exterminating USB Worms with Policy
eWeek Security Watch, By Brian Prince, Wed, 18 Aug 2010, 314 words
"The use of USB as one means of a computer worm's propagation vectors has been seen as one of the most successful (when it comes to the extent and reach of actually affected regions), and has been used not only by the USB worms per se that we usually see in the APAC regions but by other high-profile worms as well," noted Ivan Macalintal, manager of Advanced Threats Research for Trend Micro. |
| |
| Google chief admits he is worried about online privacy
The Independent, By Jerome Taylor , Wed, 18 Aug 2010, 1403 words , English
"What many people do not realise is that as soon as you put something up online you lose possession and control of that information immediately," said Rik Fergusson, a cyber security expert at Trend Micro. "Anyone can download, store and distribute that information, it's out of your hands." |
| Google chief's warning over online privacy
Channel 4 News, By Staff, Wed, 18 Aug 2010, 1308 words
Rick Fergusson predicts users will start to demand better protection in the future: "What would be ideal would be some sort of technology where you as an end user would be able to assign the right to use, copy or distribute information about yourself to people of your own choosing. That sort of technology is already used in encrypted emails. I'm sure people will start asking for some form of encrypted social networking and companies will respond to that demand." |
| |
| |
| More Android malware spotted
Web User, By Web User, Wed, 18 Aug 2010, 348 words
"The app cannot be terminated to prevent it from sending out user data. The user is thus left with only two options - to uninstall the app or to stop the SnakeService. A remote user can use another Android app known as GPS SPY to monitor a Tap Snake user's location as long as the said app is installed on the user's device," Trend Micro's Bernadette Irinco said. |
| |
|
|
| Intel to Acquire McAfee |
| The views of the industry on the Intel acquisition of McAfee
SC Magazine UK, By Dan Raywood, Fri, 20 Aug 2010, 1625 words
Eva Chen, CEO at Trend Micro, said: "Intel's decision to purchase a security software company is a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products." |
| Intel drawn to vibrant security software market McAfee buyout presents new challenge to Symantec and other security software players
Network World, By Ellen Messmer, Network World, Thu, 19 Aug 2010, 1153 words
Despite a lackluster economy, the worldwide security software industry just keeps growing. Led by Symantec, McAfee, Trend Micro, IBM and EMC, total industry sales are projected to hit at least $16.5 billion this year, up 11.3% from 2009, according to Gartner.
Editorial Comments: The story also appears at Bloomberg BusinessWeek. |
| Intel Buys McAfee: Is The PC Security Model Dead?
Dark Reading, By Rob Enderle, Fri, 20 Aug 2010, 865 words
When it comes to emerging platforms like smartphones, tablets, and embedded networked systems, the old model of separate antivirus security companies is officially dead. And Intel's purchase of McAfee puts a stake in it. |
| Intel deal for McAfee positions both firms to capitalize on mobile sector growth
Local Tech Wire, By ALAN KRANS, Technology Business Research, Thu, 19 Aug 2010, 611 words
Editor's note: Allan Krans is a senior analyst with Technology Business Research. Chip giant Intel Corporation (Nasdaq: INTC) is acquiring security firm McAfee (NYSE: MFE) in an all-cash deal worth nearly $7.7 billion. Krans analyzes the deal. |
| Intel-McAfee Deal Underscores Importance of Mobile Security
Dow Jones News Service, By Jeanette Borzo , Thu, 19 Aug 2010 11:54:00 PST, 453 words , English
SAN FRANCISCO (Dow Jones)--Intel Corp. (INTC)'s $7.7 billion bid for McAfee Inc. (MFE) highlights the growing importance of mobile security, a field that is expanding rapidly as handheld devices become more important to both consumer and ...
Editorial Comments: This story is also posted at FOXBusiness.com. |
| Intel to Acquire McAfee for $7.68 Billion
Redmond Developer, By Jeffrey Schwartz, Thu, 19 Aug 2010, 293 words
Intel will acquire security software tools supplier McAfee Inc. for $7.68 billion in cash, the company said today. The boards of both companies have agreed to the blockbuster deal, which Intel said will enable it to provide processor and network-based security.
Editorial Comments: This article also appears in Government Computer News. |
| |
| |
| Surprise: Intel Buys McAfee for $8 Billion
Channel Insider: Secure Channel, Posted by Larry Walsh, Thu, 19 Aug 2010, 420 words
News crossed the wires this morning that chip maker Intel is buying McAfee for $8 billion in cash and stock, ending one of the most anticipated corporate acquisition watches in Silicon Valley history. The surprise is that McAfee's suitor is Intel. |
| Intel's purchase of McAfee is a head scratcher
Computerworld: Security Impact, By Eric Ogren, Fri, 20 Aug 2010, 850 words
Intel's intended acquisition of McAfee for $7.68 billion is a real head-scratcher. They could have purchased comparable security technology or more attractive security businesses for much less. I don't get it, and I want to get it because I am impressed by Intel's leadership efforts with security and McAfee's pragmatic approach to endpoint security. This deal just does not make sense on so many levels, except for McAfee shareholders who were last seen in the streets hugging and giggling. |
| McAfee Security Rivals Cheer, Criticize Intel Deal
PCMag.com, By Neil J. Rubenking, Fri, 20 Aug 2010, 1317 words
Trend Micro's position is that "Intel's resources may now enable McAfee to offer protection to multiple devices and endpoints, replicating what other vendors, such as Trend Micro, have already achieved through Smart Protection Network." Trend sees Intel's acquisition as "a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products", but goes on to warn that "the embedded-software model is fundamentally different from the security-software operating model and this is a good opportunity for customers to review their relationship with their security partner to assess whether they will be receiving the services and expertise they need."
|
| |
| Intel's McAfee buy is a Buffett-like play
CNNMoney.com, By David Goldman, staff writer, Thu, 19 Aug 2010, 768 words
NEW YORK (CNNMoney.com) -- Intel's $7.7 billion purchase of security company McAfee makes plenty of financial sense, but it's a head-scratcher from a technology standpoint. |
| |
| |
|
|
| Underground Clearing House |
| |
| Credit Card Clearing House Hacked Says Security Researchers
The New New Internet, By Michael W. Cheek, Mon, 16 Aug 2010, 153 words
An underground credit card clearing house has been hacked, according to Trend Micro security researchers. Leaked data from the hack include employee emails and recorded phone calls. |
| Cybercriminals Uneasy After Underground Payment Processor Breached
Softpedia, By Lucian Constantin, Security News Editor, Tue, 17 Aug 2010, 273 words
Many cybercriminals are probably nervous after an unidentified group of hackers managed to compromise a credit card payment processor used in illegal operations and leaked detailed information about its customers. |
| |
| |
|
|
| Trend Micro Mentions |
| Messing with Internet scammers
Help Net Security, By Zeljka Zorz, Fri, 20 Aug 2010, 471 words
Online scammers are resourceful people who take advantage of people's gullibility and lack of knowledge about Internet dynamics, but once in a while they happen to stumble upon users who will know who they are dealing with and are willing to play along and lead them on a merry chase. Trend Micro researcher David Sancho is one of those. Admittedly, it's his job to do so, but it is nevertheless very nice to see an intended victim waste the spammers' time. |
| Insider: The world of security evangelism
The Tech Herald, By Steve Ragan, Tue, 17 Aug 2010, 1016 words
Other examples of positive evangelistic usage, based on our experiences with them, come from Sean-Paul Correll, who is with Panda Labs, and David Perry from Trend Micro. There are some bad examples as well, but we will avoid naming them here. They know who they are. |
| 10 Tools To Speed Windows 7 Trend Micro Housecall
CRN, By Staff, Wed, 18 Aug 2010, 117 words
We've been using Housecall for years--it's Trend Micro's free, online malware-scanning tool. While other vendors provide free online virus scans, Trend Micro's, we've found, is among the fastest and most robust--and it's worked for us in the CRN Test Center for so long, it's long ago passed the threshold of trustworthy technology. The caveat is that a PC that's infected and can't access the Internet can't make use of this online scan (for obvious reasons) |
| Avnet Plans To Buy Australian Distributor itX
CRN, By Scott Campbell, CRN, Mon, 16 Aug 2010, 196 words
Avnet (NYSE:AVT) has agreed to acquire itX Group, an Australian distributor for $69.2 million in cash. itX distributes software, hardware and services from vendors including IBM (NYSE:IBM), Hewlett-Packard (NYSE:HPQ), VMware, Apple (NSDQ:AAPL), Citrix (NSDQ:CTXS), Red Hat, and Trend Micro. The company generated about $131.5 million in sales for the fiscal year ended June 30 and has about 150 employees and six locations I Australia. |
| |
| Popular AV Solutions Miss Most Malware
SPAMfighter News, By Staff, Sat, 14 Aug 2010, 364 words
In its latest report on Internet security, Cyveillance Inc. a contractor for cyber intelligence based in Arlington (USA) states that conventional anti-virus software are still lagging behind cyber-criminals insofar as spotting as well as safeguarding against rapidly-evolving and fresh attacks from malware are concerned. |
| Gadgets | for college-bound students
The Milwaukee Journal Sentinel, STANLEY A. MILLER II, smiller@journalsentinel.com; Milwaukee Journal Sentinel , Sun, 15 Aug 2010, 1612 words , English
Some students need more mobile storage than others, and that where Iomega's Skin eGo portable hard drives. These come in three bold designs - mostly black, mostly red or mostly silver - and offer monstrous storage of 500 GB. Yet measuring 4.88 inches by 3.35 inches by 0.69 inches, they take up little desk or backpack space, and at 0.36 pounds, are easily toted. The drives are self-powered, connect to a computer via USB 2.0 and compatible with Windows XP, Mac OS X 10.4 and beyond. Each comes with a suite of downloadable security software to protect the drive's contents that includes Trend Micro Internet Security and EMC Retrospect Express Backup software. They cost $119.99 at iomga.com, which also lists several online and national retailers.. |
| Get a 1TB Iomega USB hard drive for $60 shipped
CNET: The Cheapskate, By Rick Broida, Wed, 18 Aug 2010, 343 words
I know cheap 1-terabyte hard drives are getting to be old hat these days, but you have to understand: I can remember when the PC reseller I once worked for was able to offer a 250-megabyte drive for $250, and what a big deal that was. |
| Click Fraud Trojans - A Profitable Business
SPAMfighter News, By Staff, Wed, 18 Aug 2010, 391 words
Security experts at Trend Micro have discovered that click fraud conducted through medium-sized botnet is a profitable business that can earn millions of dollars on an annual basis. |
| Anti-Virus Suite Protection? Not Much
InformationWeek's Security Blog, Posted by George Hulme, Wed, 18 Aug 2010, 411 words
It's no secret that anti-virus software doesn't do much to protect you against new and rapidly moving viruses, so it shouldn't come as much of a surprise that these suites don't do much good defending you against exploit code, either. A fresh evaluation from NSS Labs reveals just how vulnerable you really are. (Trend Micro) |
| AV-Test Certifies Security Products on Windows 7
Redmondmag.com, By Kurt Mackie, Wed, 18 Aug 2010, 754 words
AV-Test this week published certification results for 19 software security products running on Windows 7. The test and consulting firm ranked the 19 antimalware products based on three categories: protection, repair and usability. Three products failed to get certified, including BullGuard Internet Security 9.0, McAfee Internet Security 2010 and Trend Micro Internet Security Pro 2010.
Editorial Comments: This article also appears in Government Computer News. |
| Fake Windows MSRT Utilized For Spreading Scareware
SPAMfighter News, By Staff, Fri, 20 Aug 2010, 357 words
Researchers at security firm Trend Micro have detected a phony MSRT (Malicious Software Removal Tool), which displays the real icon belonging to the original application. |
| Liverpool vs Trabzonspor LIVE Stream!
News By The People, By admin., Thu, 19 Aug 2010, 234 words
Posted in Soccer News, Sports - The August 19th, 2010 match between Liverpool and Trabzonspor is currently underway, and is set to be a great match-up. Liverpool is currently without Javier Mascherano and Daniel Agger, due to injuries. Manchelivarse.com reports that Fernando Torres could make his first start today. |
| Depositing Security FUD
About.com: Antivirus Software, By Mary Landesman, Antivirus Software Guide, Fri, 20 Aug 2010, 121 words
It's unfortunate, but some marketeers thrive on perpetuating Fear, Uncertainty, and Doubt. One timely example, Trend Micro's recent news release titled "ATMs - Can You Bank on Their Safety?". Referring to a demonstration at the August 2010 Black Hat conference, the article proclaims, "One attack required a few seconds for the cybercriminal to open the ATM and insert a USB drive with a code to overwrite its system." |
| Tech 2.0 for Tuesday, August 17
KPVI News 6, By Matt Davenport, Senior Tech Specialist, Tue, 17 Aug 2010, 114 words
Tech 2.0 Extra: The new "Starcraft" game dominated software sales in the past month. "PC Starcraft II: Wings of Liberty" is the top-selling software for July, according to NPD Group. "Kaspersky Antivirus 2010," "Webroot AntiVirus w/Spy Sweeper 2010" and "Trend Micro AntiVirus 2010 Plus Anti-Spyware" bump down one place each to numbers two, three and four. "MS Office 2010 Home & Student 3User" is in fifth place, followed by "PC Starcraft II: Wings of Liberty Collector's Ed." In seventh is "MS Office 2010 Home & Student Product Key Card." "Norton 360 4.0 3User" is number eight, "iWork 2009" is ninth and "MobileMe" is number ten.
|
| |
|
|
| Full Text |
| |
| "The use of USB as one means of a computer worm's propagation vectors has been seen as one of the most successful (when it comes to the extent and reach of actually affected regions), and has been used not only by the USB worms per se that we usually see in the APAC regions but by other high-profile worms as well," noted Ivan Macalintal, manager of Advanced Threats Research for Trend Micro.
- - -
Malware spreading via USB devices is not a new phenomenon, but it is still effective.
According to McAfee's 2010 Q2 Threat Report, the most widely detected threat was the Genericlatr Trojan, AutoRun malware found on nearly 9 percent of machines scanned by the company worldwide. Then there is Stuxnet, Conficker and other malicious threats that have taken advantage of lax policies toward removable devices.
For enterprises and home users alike, it is important to lock down the attack vector.
"The use of USB as one means of a computer worm's propagation vectors has been seen as one of the most successful (when it comes to the extent and reach of actually affected regions), and has been used not only by the USB worms per se that we usually see in the APAC regions but by other high-profile worms as well," noted Ivan Macalintal, manager of Advanced Threats Research for Trend Micro.
Though policies are only half the battle, as illustrated here, there are certain things businesses should do. For one, organizations should disable the AutoRun feature for all removable devices. In addition, enterprises should make sure the use of USB drives is permitted only when necessary, advised Kevin Haley, director of Symantec Security Response.
Also, "if network shares are required then use unique non-intuitive passwords for their access [and] configure client security applications to scan devices when they are attached," Haley suggested.
http://securitywatch.eweek.com/online_malware/exterminating_usb_worms.html
|
| Back to top |
|
|
| |
| The malware on the Spanair computer has been identified as a type of Trojan horse. It could have entered the airline's system in a number of ways, according to Jamz Yaneeza, head threat researcher at Trend Micro.
- - -
Authorities investigating the 2008 crash of Spanair flight 5022 have discovered a central computer system used to monitor technical problems in the aircraft was infected with malware.
An internal report issued by the airline revealed the infected computer failed to detect three technical problems with the aircraft, which if detected, may have prevented the plane from taking off, according to reports in the Spanish newspaper, El Pais.
Flight 5022 crashed just after takeoff from Madrid-Barajas International Airport two years ago today, killing 154 and leaving only 18 survivors.
The U.S. National Transportation Safety Board reported in a preliminary investigation that the plane had taken off with its flaps and slats retracted — and that no audible alarm had been heard to warn of this because the systems delivering power to the take-off warning system failed. Two earlier events had not been reported by the automated system.
The malware on the Spanair computer has been identified as a type of Trojan horse. It could have entered the airline's system in a number of ways, according to Jamz Yaneeza, head threat researcher at Trend Micro.
Some of the most likely ways are through third party devices such as USB sticks, Yaneeza said, which were responsible for the International Space Station virus infection in 2008, or through a remote VPN connection that may not have the same protection as a computer within the enterprise network. Opening just one malicious file on a single computer is all it takes to infect an entire system.
"Any computer that is connected to a network is vulnerable to a malware infection," O. Sami Saydjari, president of Cyber Defense Agency, told TechNewsDaily. "Standards have not been set to protect critical infrastructure."
An incident like this could happen again, and most likely will, according to Saydjari.
A judge has ordered Spanair to provide all of the computer's logs from the days before and after the crash.The final report from crash investigators is not due to be presented until December.
http://www.msnbc.msn.com/id/38790670/ns/technology_and_science-security/
|
| Back to top |
|
|
| |
| News
ERIC SCHMIDT, the chief executive of Google, has issued a stark warning over the amount of personal data people leave on the internet and suggested that many of them will be forced one day to change their names in order to escape their cyber past. In a startling admission from a man whose company has made billions by perfecting the art of hoarding, storing and retrieving information on us, Mr Schmidt suggested that the enormous quantity of detail we leave online may not be such a good thing after all.
The man who - alongside Google's founders Sergey Brin and Larry Page - runs the world's largest search engine said that young people will need to go as far as changing their identities if they are to truly erase what they have left online.
"I don't believe society understands what happens when everything is available, knowable and recorded by everyone all the time," he told the Wall Street Journal. "I mean we really have to think about these things as a society."
For a man whose company is built on the ability to store information and retrieve it again in a faster and more efficient way than its rivals, Mr Schmidt's admission revealed a surprising concern among Google's leadership over the importance of data privacy.
But it has also provoked a wider debate on the sheer amount of information we give away about ourselves online and how most of that data is virtually un-erasable.
Perhaps more than any other company Google has helped created a world where we willingly deposit vast amounts of personal data into the public domain - information that might previously have taken months of investigative work by professionals to find.
Google has made billions from storing data on its customers' browsing habits so that it can use that data to target them with personalised adverts. It also runs the kind of websites that have pioneered the open sharing of information online. The Californian internet giant owns You Tube, the world's largest video sharing website; it handles billions of our emails through Gmail; and - if you live in a big city - chances are that a Google Street View car has photographed your front door. A series of recent acquisitions also suggests it is hoping to move into the social networking market, the area of the internet that most concerns privacy campaigners.
Thanks to the global popularity of social networking - an estimated 600 million people have personal online profiles - friends, prospective employers and enemies alike are able to access photographs, videos and blogs that we may have long forgotten with a few simple clicks of a mouse. Recently one columnist in The New York Times went so far as to describe our current world as an age defined by "the impossibility of erasing your posted past and moving on".
Many websites yesterday picked up on the apparent disconnect between Mr Schmidt's comments and his company's ethos.
Chris Williams, of the online tech news website The Register, said: "Recording everything and making it knowable by everyone all the time is Google's stated mission, and it is profiting handsomely from the fact that society doesn't understand the consequences."
Other blogs remarked that one previous instance when Mr Schmidt had admitted concerns over the amount of personal information stored online was in 2005 when Google blacklisted the online technology magazine Cnet for an entire year.
In an article discussing privacy concerns generated by Google's data mining capabilities, Cnet's reporters published Mr Schmidt's salary, named the neighbourhood where he lives, some of his hobbies and political donations. All the information had been gleaned from Google searches.
But while bloggers and web forums reacted with tangible scepticism to Mr Schmidt's comments, others welcomed his frankness.
"His comments are a little ironic but they are also timely," said Dylan Sharpe from Big Brother Watch, which has campaigned against Google collecting wifi data on web users while taking photographs with its Street View cars.
He added: "Google is a company that specialises in knowing where you are, what you are doing and who you are talking to. That's a scary prospect even though Google's users sign up to this sort of data collection willingly.
"But Mr Schmidt is completely right on how much information we are giving away online. Right now there are millions of young kids and teenagers who, when they apply for jobs in 10 years' time, will find that there is so much embarrassing stuff about them online that they cannot take down."
Those who wish to delete what they have put up online, meanwhile, may find it next to impossible to entirely erase their cyber past.
"What many people do not realise is that as soon as you put something up online you lose possession and control of that information immediately," said Rik Fergusson, a cyber security expert at Trend Micro. "Anyone can download, store and distribute that information, it's out of your hands."
Privacy campaigners say more needs to be done to stop young people in particular depositing information online that may come back to haunt them.
"I think we need to change people's mindsets through education rather than legislation but it's definitely something that we need to talk to our children about," said Mr Sharpe.
Mr Fergusson, meanwhile, believes web users will increasingly demand better levels of data privacy over the coming decade.
"What would be ideal is some sort of technology where you as an end user would be able to assign the right to use, copy or distribute information about yourself to people of your own choosing," he said. "That sort of technology is already used in encrypted emails. I'm sure people will soon start asking for some form of encrypted social networking and companies will respond to that demand."
IN HIS OWN WORDS
The internet is the first thing that humanity has built that humanity doesn't understand, the largest experiment in anarchy we've ever had.
Show us 14 photos of yourself and we can identify who you are. You think you don't have 14 photos of yourself on the internet? You've got Facebook photos! People will find it's very useful to have devices that remember what you want to do, because you forgot ... But society isn't ready for questions that will be raised as a result of user-generated content.
When the internet publicity began, I remember being struck by how much the world was not the way we thought it was, that there was infinite variation in how people viewed the world.
People are surprised to find out that an awful lot of people think that they're idiots.
CASE STUDY
'Drunken pirate' lark destroyed teaching career
The tale of Stacy Snyder, the "drunken pirate", is a cautionary one for any young person hoping to embark on a promising career.
Ms Snyder, a trainee teacher, had passed all her exams and completed her training. Her academic record was unblemished. That is, until her final summer, when her teachers - out of the blue - deemed that the behaviour she had displayed in her personal life was unbecoming of a teacher.
Her crime? She had uploaded an image of herself, wearing a pirate costume and drinking from a plastic cup on to a social networking site with the caption: "drunken pirate."
A colleague at the school where she had been training had seen it and reported it, saying that it was unprofessional to potentially expose pupils to photographs of a teacher drinking alcohol.
As university officials told her that her dream career was now out of her reach, she offered to take the photo down, and argued that it was not even possible to see what was in the cup. After all, she told them, "is there anything wrong with someone of a legally permissable age drinking alcohol?"
But her pleas were ignored. Ms Snyder never got the certificate she needed to teach and an attempt to sue the university for it was unsuccessful.
Placing a photograph of herself in "an unprofessional state" was her downfall: the image had been catalogued by search engines and by the time she realised the danger, it was impossible to take down.
KEVIN RAWLINSON |
| Back to top |
|
|
| |
| Rick Fergusson predicts users will start to demand better protection in the future: "What would be ideal would be some sort of technology where you as an end user would be able to assign the right to use, copy or distribute information about yourself to people of your own choosing. That sort of technology is already used in encrypted emails. I'm sure people will start asking for some form of encrypted social networking and companies will respond to that demand."
- - -
As Google's chief executive Eric Schmidt warns about the shortfalls in online privacy protection, the pan-European Insafe Network tells Channel 4 News more needs to be done to educate children about the risks of sharing details online.
With many social media websites still in their youth - such as Facebook which launched in 2004 - the perks and pitfalls of sharing personal information online are still being discovered by users across the globe.
Now Google's chief executive has spoken out to warn users of the dangers of putting personal information into the public domain.
Google's chairman and CEO Eric Schmidt said: "I don't believe society understands what happens when everything is available, knowable and recorded by everyone all the time. I mean, we really have to think about these things as a society."
Google itself trades and profits on the collection, storage and retrieval of personal information – and Mr Schmidt's concerns are certainly not new.
Dylan Sharpe of the organisation Big Brother Watch backed up Mr Schmidt's comments stating: "(He) is completely right on how much information we are giving away online. Right now there are millions of young kids and teenagers who, when they apply for jobs in 10 years time, will find that there is so much embarrassing stuff about them online that they cannot take down."
The internet: records everything, forgets nothing
There was a time when our past actions were confined to memories, and memories fade. Everyone has done things they would rather forget: people grow, develop and change over time. The problem, say privacy campaigners, is that when past behaviours or events have been recorded - be it in the form of messages or photos - it makes it harder to forget.
Online and social media revolutions have provided us with myriad ways to reveal information about ourselves. An estimated 600 million people now have online profiles on which they make personal details available to friends, friends of friends, employers, prospective employers, and even enemies. Twitter, Facebook, MySpace and Bebo all encourage us to share; but is it safe to give ourselves away like this?
Tracking your online presence:
One man has made an online record of every document, every location and even every conversation that he has had over the past decade. Channel 4 News science correspondent Tom Clarke meets Gordon Bell - one of the pioneers of the World Wide Web - to find out why such total recall is necessary.
Click here to read the article in full
Rick Fergusson of internet security firm Trend Micro warns that, while it may seem like fun, when something is posted online we lose ownership over it. Photos and conversations can be stored and passed on by anyone who has access, and we can lose track of what is out there.
According to a survey by Microsoft, 75 per cent of recruiters and human resorces professionals in the US say their companies require them to do online research about candidates, for which they scrutinise social networking sites, photo and video-sharing sites and personal websites and blogs.
Stacy Snyder
Four years ago American trainee teacher Stacy Snyder found herself the victim of online sharing. A photo of her bearing the caption 'drunken pirate' and showing her wearing a pirate hat and holding a plastic cup was picked up by a colleage from her MySpace account. Ms Snyder's supervisor told her the photo was "unprofessional" and amounted to her promoting drinking. This behaviour was deemed "inappropriate" by the school and she was denied her teaching degree.
Ms Snyder argued that the university has violate her rights by penalising her for personal activity that was perfectly legal. But in 2008 her claim was rejected; she was effectively barred from entering her chosen profession.
Online footprints
The concern over this issue has manifested itself in recent years in the emergence of companies offering services to "clean up" personal online histories. Companies like ReputationDefender offer to extensively search for you online and permanently erase anything incriminating from the world wide web.
"Looking on the first page of Google is not enough" the ReputationDefender website proclaims: "Our agents perform a customised monthly search of the far corners of the Deep Web for every reference to you, including over 40 of the biggest social networks. A customised search for every reference to you on the web gives you total awareness of your online presence. We continue to monitor the Deep Web for any new reference to you and provide an alert. Our agents will work with you to identify the good, the bad and the inaccurate."
But while technology may advance enough to allow references to be removed, when it's out there its out there and you never know who has kept hold of it.
Rick Fergusson predicts users will start to demand better protection in the future: "What would be ideal would be some sort of technology where you as an end user would be able to assign the right to use, copy or distribute information about yourself to people of your own choosing. That sort of technology is already used in encrypted emails. I'm sure people will start asking for some form of encrypted social networking and companies will respond to that demand."
Campaigning for privacy
Computers have become a permanent fixture in our lives, and users are getting younger. A recent survey by Ofcom revealed that in the UK 75 per cent of five to seven year olds are already online. 22 per cent of eight-11 year olds have a solution networking profile.
Janice Richardson, senior adviser at European Schoolnet and coordinator of the pan-European Insafe network which campaigns for online education for children, told Channel 4 News: "By using computers children have access to very powerful tools and although there are legal instruments to protect their privacy, often they don't fully understand the concept of privacy and how those laws work.
"Technology today offers great opportunities but there are serious potential repercussions. When an item is shared, be it a message or a photo on a social networking site or a mobile phone, ownership is immediately lost.
"Children go to school to socialise and learn what they can and can't do in society, yet schools are no longer in step with children's reference points in today's information society. Just ten years ago it was easier to understand what information you should or shouldn't give away, what was for family and what was for friends. But the internet and other technologies blur those lines.
The Insafe network is campaigning to educate children about safe use of the internet, to make them think before they post. The organisation is currently working on an activity book for four to eight year olds to help fill this gap. Parents can find useful activities for their children on these issues at www.esafetykit.net
Your online future
Logic would dictate users have three options: don't publish information, try and manage the information later, or hope that in the future society just will not care what is out there.
All users have the potential to be haunted by their cyber past and experts warn some may find they have to change their names and identities in the future if they really want to get away from what is posted online.
http://www.channel4.com/news/articles/science_technology/google+chiefaposs+warning+over+online+privacy/3747277
|
| Back to top |
|
|
| |
| Very interesting. "But Mr Schmidt is completely right on how much information we are giving away online. Right now there are millions of young kids and teenagers who, when they apply for jobs in 10 years' time, will find that there is so much embarrassing stuff about them online that they cannot take down."
Those who wish to delete what they have put up online, meanwhile, may find it next to impossible to entirely erase their cyber past.
"What many people do not realise is that as soon as you put something up online you lose possession and control of that information immediately," said Rik Fergusson, a cyber security expert at Trend Micro. "Anyone can download, store and distribute that information, it's out of your hands."
Ms Snyder, a trainee teacher, had passed all her exams and completed her training. Her academic record was unblemished. That is, until her final summer, when her teachers – out of the blue – deemed that the behaviour she had displayed in her personal life was unbecoming of a teacher.
Her crime? She had uploaded an image of herself, wearing a pirate costume and drinking from a plastic cup on to a social networking site with the caption: "drunken pirate."
Ms Snyder never got the certificate she needed to teach and an attempt to sue the university for it was unsuccessful.
http://www.americablog.com/2010/08/google-chief-warns-of-internet.html |
| Back to top |
|
|
| |
| "No malware for a mobile device has been known to do that before," said Rik Ferguson, senior security advisor for Trend Micro.
- - -
Your smartphone is like a miniature computer, getting smarter and more powerful while enabling greater functionality with each new mobile device that is released. It's exciting to customize your cell phone with any type of application you want. Google and Apple, alone, offer more than 250,000 apps such as games, productivity and financial tools, and other apps. In fact, the apps craze is moving at such a fast pace, it might prove difficult to keep up with the malicious software that is sometimes a "bonus" in the app download. One thing is certain, your cell phone is not safe. Mobile phones are now targeted by malware writers and cell phones can even be lassoed into botnets.
"Mobile phones are a huge source of vulnerability," Gordon Snow, assistant director of the Federal Bureau of Investigation's Cyber Division, told the Wall Street Journal. "We are definitely seeing an increase in criminal activity." Snow also told WSJ that the FBI's Cyber Division is working on cases based on tips about malicious apps that can compromise banking or be used for espionage. The FBI does not allow its employees to download apps on FBI-issued smartphones.
After the Schmoocon hacker conference last year, security researchers presented a vulnerability that was considered so dangerous to Google's mobile OS Android that owners were warned not to use the phone's web browser. And now the Android is being hit with its first SMS trojan in the wild. It seems Android owners are getting wise about protection at a rapid pace. DroidSecurity's free antivirus was clocked at 2.5 million downloads last week.
Last year at Black Hat security conference, researchers were able to attack an iPhone via SMS. "Consumers should be aware that iPhone security is far from perfect and that a piece of software downloaded from the App Store may still be harmful," wrote software engineer Nicolas Seriot in a research paper detailing iPhone security holes.
Apple, Blackberry, Android, Windows mobile, and Symbian smartphones all have been under siege; none are immune from attacks. Yet we can't quench our desire for apps. So what is a cell phone owner to do? Think of it sort of like safe sex. You can still engage in it, but you need to be wise and to take precautions in order to avoid complications.
Sex and "sexy malware" played a part in one of the first alerts of mobile botnets aimed at the Symbian. Sexy Space was a variant of another mobile malware called Sexy View. It was capable of downloading new SMS templates from a remote server in order to send out new SMS spam. "No malware for a mobile device has been known to do that before," said Rik Ferguson, senior security advisor for Trend Micro. Trend Analysts had "heated internal discussions" about whether Sexy Space qualified as botnet code. It took a little bit of social engineering to get users onto a malicious site where it was unknowingly downloaded. Part of its lure was that the vendor seemed to point to "Playboy." Many users were caught without protection and voila! Sexy mobile malware gave a whole new meaning to phone sex.
Speaking of sex and phones, the dating site OKCupid.com conducted research on nearly 10,000 smartphone users. iPhone owners are getting much more sex than Blackberry or Android owners. Women iPhone users get the most action of anyone. OkCupid's results are listed on the graphs below. (Click on the image for a larger view)
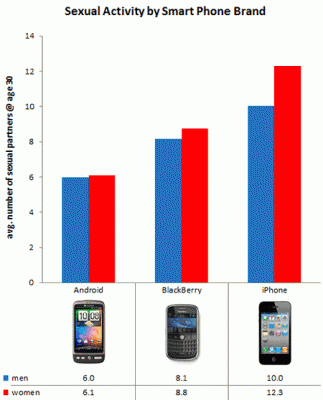
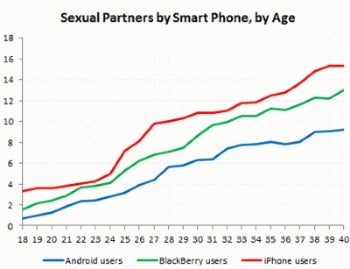
It may prove interesting to see if the heaviest hit mobile malware sectors will mirror this sex and cell phone study, with iPhone on top, followed by Blackberry and then Android. Take precautions; be wise before you take "home" an app that you don't know well enough to trust. And by all means, please use protection!
http://www.pcworld.com/article/203303/sexy_malware_bound_for_smartphones.html?tk=hp_new
|
| Back to top |
|
|
| |
| "The app cannot be terminated to prevent it from sending out user data. The user is thus left with only two options - to uninstall the app or to stop the SnakeService. A remote user can use another Android app known as GPS SPY to monitor a Tap Snake user's location as long as the said app is installed on the user's device," Trend Micro's Bernadette Irinco said.
- - -
Security experts have warned owners of Android-based handsets not to install an app going by the name of Tap Snake.
Malware targeting the Android mobile phone operating system that is capable of spying on your location has been spotted posing as a legitimate app, according to security experts.
The malicious app is called Tap Snake and has been circulating in the Android market.
Disguised as a version of the popular game Snake it begins reporting the location of the handset once you accept the end-user licence agreement (EULA).
Users of another Android app would then be able to track your every move, security researchers said.
"The app cannot be terminated to prevent it from sending out user data. The user is thus left with only two options - to uninstall the app or to stop the SnakeService. A remote user can use another Android app known as GPS SPY to monitor a Tap Snake user's location as long as the said app is installed on the user's device," Trend Micro's Bernadette Irinco said.
The company advised anyone installing an app, no matter what platform, should carefully read the EULA to check exactly what they were agreeing to.
"Tap Snake does not require GPS data yet asks for permission related to it in its EULA. This should thus prompt users to be wary of installing the app," Irinco said.
Last week, the first ever Android SMS Trojan was spotted circulating in the wild.
Security experts said that the SMS Trojan would send multiple messages to a premium-rate number, running up big bills for those unfortunate enough to pick up the infection.
http://www.webuser.co.uk/news/top-stories/496150/more-android-malware-spotted
|
| Back to top |
|
|
| |
| Eva Chen, CEO at Trend Micro, said: "Intel's decision to purchase a security software company is a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products."
- - -
Yesterday's huge announcement that Intel is to purchase McAfee for $7.7 billion was one of the biggest stories in this industry this year.
The acquisition brought some interesting perspectives from across the technology spectre, and here we look at some of the comments on it.
From an analyst perspective Leslie Fiering, research VP at Gartner, called it a 'smart strategic move' and said that it was 'part of a larger strategy to enhance Intel's security capabilities, as it follows other recent acquisitions of tenCube and Trust Digital'.
She said: "The goal is to collect and develop IP that can go directly to silicon and bring security down to the hardware level. The embedded security will run outside the OS with a broad variety of software developer hooks. It is highly unlikely that Intel will make any of these proprietary or in any way specific to McAfee.
"Bringing security down to the hardware level is particularly critical at a time when exploits at the OS level are getting more sophisticated on PCs and mobile OSs are still highly immature in the security arena. This move particularly enhances Intel's mobility strategy by adding security as a differentiator as the company girds up to combat the incumbents in the smartphone, ATM, appliance and embedded processor markets."
However Forrester's Andrew Jaquith described it as a 'horseless carriage vendor buys buggy-whips', commenting that the price is not so high that it makes Intel look like Daddy Warbucks, but not so low that it looks like McAfee was desperate to sell.
He said: "Everyone agrees that mobility is huge, and that the post-PC market will eventually eclipse today's PC market. Indeed, Forrester data shows that the crossover point is this year. Intel knows this, so it wants to plant a flag in the mobile security space as it believes will be necessary to protect these new devices.
"Moreover, I can understand why Intel feels it ought to be baking more capabilities into silicon: it helps differentiate its chips against rivals AMD and ARM (via its licensees). Adding more functionality to core offerings as a way to entice buyers to upgrade to their platform is a classic strategy that Intel's acquisition target (McAfee) has been perfecting for years with its desktop anti-malware suite.
"That product started as a humble virus scanner. Today it includes anti-spyware, a host firewall, data leak prevention, host intrusion prevention and much more. What McAfee has done on the desktop, Intel intends to do 'inside', on its silicon."
He commented that he could see four problems with Intel's strategy: that neither Intel nor McAfee are serious players in the mobility market and this deal does not improve their prospects; that Intel's hardware platform strategy will not work as most enterprises take the least-common-denominator approach to managing their computing assets; that Intel does not understand software; and that the security aftermarket will be very different on post-PC devices.
He said: "All of which leads me to conclude that while Intel's stated rationales for doing the McAfee deal are very forward-looking, its likely actual revenues are mostly about the past. If Intel wants to grow the franchise for protecting PC platforms, the McAfee deal is a great acquisition.
"If you view today's security aftermarket as something that ought to be better left in the ashbin of history, where security is baked into operating systems, this deal is more of a head-scratcher."
Blogger Bruce Schneier said that the deal was 'another example of a large non-security company buying a security company', that he has been talking about for two and a half years.
He said: "It's not consolidation as we're used to. In the security industry, there are waves of consolidation, you know, big companies scoop up little companies and then there's lots of consolidation. You've got Symantec and Network Associates that way, and then you have 'best of breed' where a lot of little companies spring up doing one thing well and then you cobble together a suite yourself.
"What we're going to see is consolidation of non-security companies buying security companies. So, remember, if security is going to no longer be an end-user component, companies that do things that are actually useful are going to need to provide security.
"So, we're seeing Microsoft buying security companies, we're seeing IBM Global Services buy security companies, my company was purchased by BT, another massive global outsourcer. So, that sort of consolidation we are seeing, it's not consolidation of security; it's really the absorption of security into more general IT products and services."
From a security perspective, Don Smith, VP of engineering and technology at SecureWorks, claimed that it is not as surprising an acquisition as you might first think, as Intel has a number of security technologies, which span from secure virtualisation to secure XML gateways.
Proofpoint looked at the statements made and identified that McAfee's announcement, which said that 'the current cyber security model is not extensible across the proliferating spectrum of devices – providing protection to a heterogeneous world of connected devices requires a fundamentally new approach to security', is a way of saying that network security in today's world needs a major 're-think'.
It also said that certain security functions and controls need to migrate further down the IT application stack and be more of an integral part of the hardware and firmware that power new devices.
It also claimed that it expected this news to spur ongoing M&A activity in the security space and more importantly, the trend toward making security more of a core component of computing devices—rather than an afterthought—will make for a safer computing world.
Rob Rachwald, Imperva's director of security strategy, claimed that the acquisition means one thing, that security cannot be separated from the business.
He said: "In the past, the objective of security was all about keeping the bad guys out while letting the good guys in. However, with the advent of insiders and as external hacking's focus shifted to data theft, the objective of security professionals changed dramatically.
"Data, and the transactions that moved data, meant security teams had to deploy security as a part of supply chains, online transactions and for online collaboration among customers, employees, partners and social networks."
Philippe Courtot, chairman and chief executive officer of Qualys, commented that the acquisition is another example of the rapid consolidation taking place in the enterprise software industry, as traditional high tech vendors have an increasingly harder time competing against SaaS and cloud computing offerings and can only find growth by embarking on aggressive pricing against their competitors to steal market share.
Eva Chen, CEO at Trend Micro, said: "Intel's decision to purchase a security software company is a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products.
"For current and future customers, Intel's resources may now enable McAfee to offer protection to multiple devices and endpoints, replicating what other vendors, such as Trend Micro, have already achieved through the Smart Protection Network.
"However, the embedded-software model is fundamentally different from the security-software operating model and this is a good opportunity for customers to review their relationship with their security partner to assess whether they will be receiving the services and expertise they need."
Pat Clawson, CEO of Lumension, commented that the acquisition will not only fundamentally change the security landscape, but will have a ripple affect throughout the industry.
He said: "With this acquisition, Intel is addressing areas that we really need to get better at protecting - smartphones, televisions, medical technology and cash machines. Short term, it gives Intel a competitive advantage but will no doubt make other chip manufacturers, like AMD, consider whether they need to mirror the acquisition.
"For the security industry, it makes the top layer of the security stack – such as Symantec – obvious acquisitions targets not only for chip manufacturers but also hardware providers, such as mobile device manufacturers. On the flip side, it could leave a waste land of security companies, as mid-sized security companies see a diminishing number of prospective acquirers."
Graham Cluley, senior technology consultant at Sophos, commented that this marks a return to the security sector for Intel after it sold its own anti-virus product (Intel LanDesk Virus Protect) to Symantec in 1998.
He said: "Now, Intel is purchasing Symantec's arch-enemy McAfee and re-entering the business. It's too early to say what the impact of this acquisition will mean to McAfee's customers, but there will no doubt be some happy McAfee shareholders today as the price rises to its highest level since the late 1990s."
Ron Gula, CEO of Tenable Network Security, said: "I'm curious to see what Intel's commitment to enterprise security software will be post-acquisition. McAfee is best known for its anti-virus solution, but their large-scale security technologies aren't something I see Intel leveraging.
"There are a lot of things wrong with today's anti-virus model, such as tracking the sheer number of potential bad types of software. Putting this into hardware may sound promising, but I question how much can be placed into a chip.
"If Intel can move the anti-virus agent into hardware, I'd like some assurances that this can be patched when a security vulnerability is found with it. Anti-virus software is very complex and we often run into customers whose agents are one or two patch levels behind and open to attack. Patching hardware or firmware is much harder than patching software."
http://www.scmagazineuk.com/the-views-of-the-industry-on-the-intel-acquisition-of-mcafee/article/177214/
|
| Back to top |
|
|
| |
| Despite a lackluster economy, the worldwide security software industry just keeps growing. Led by Symantec, McAfee, Trend Micro, IBM and EMC, total industry sales are projected to hit at least $16.5 billion this year, up 11.3% from 2009, according to Gartner. Into this security sales fest steps Intel with its Thursday morning announcement that it plans to acquire McAfee for $7.68 billion. Intel CEO Paul Otellini indicated that the companies have been working closely over the past 18 months and hinted that security features related to Intel processors will arrive by early next year.
"Everywhere we sell a microprocessor, there's an opportunity for a security suite," Otellini said during a press conference on the planned buyout, adding there could be further integration of McAfee technologies into Intel products.
In a blog post, George Kurtz, McAfee's worldwide CTO and executive vice president, pointed to whitelisting capabilities of SolidCore, a McAfee acquisition, as a good fit with Wind River, the embedded and mobile software vendor that Intel acquired last year.
Intel sees a huge future in the advance of mobile devices and McAfee has also made it a priority this year to further its mobile management and security strategy via acquisitions of its own.
McAfee, which will operate as a separate subsidiary, is Intel's pick to complement the work Intel has already done on its hardware-based security, vPro. But Otellini did stress during the press conference that Intel is also open to working with other security vendors.
Still, a Intel-McAfee union could mean a tougher security software market for big and small vendors alike.
Symantec, whose products extend into storage, backup and services, holds just over 20% of the security software market worldwide, and while that's not bad, it's actually down from the 24.11% share it had in 2007 and the company recently warned of cautiousness among tech buyers. Not only are traditional rivals such as McAfee and Trend Micro bearing down, but IBM, EMC/RSA and Cisco now seem more determined to play the role of main security vendor for the enterprise.
In this superheated competition, IBM also plays the role of partner to both Symantec and McAfee at times, and giant HP is a conduit to the customer through its security-services division gained through the EDS acquisition.
"The competitive landscape for us is changing," acknowledged Bill Robbins, Symantec executive vice president of worldwide sales, recently discussing the overall market.
Symantec itself just spent many millions to buy PGP, GuardianEdge and VeriSign's authentication business to get encryption and certificate technologies. (Trend Micro will soon be unveiling some encryption-related plans as well.)
Such diversification isn't a bad idea, since selling security to the enterprise is increasingly a matter of having lots of different enticements to offer the customer -- sometimes a giveaway in a bundled offering. "I've seen deals where the encryption is free," noted Gartner analyst Neil McDonald discussing the topic recently.
Showing up to woo the customer with as much as possible -- storage, backup, desktop security suites and services -- is increasingly the fashion. "We'll say to the CIO, here's our vision, here's what we can do today and what's on the roadmap," Robbins said.
Price completion is fierce, according to some.
Evansville, Ill.-based manufacturer Berry Plastics, which has been using Symantec's PureDisk de-duplication and NetBackup in its data center, as well as Altiris management, invited Symantec in to bid against McAfee for an enterprise-wide desktop security contract for over 5,000 desktops .
Shane Mers, systems team supervisor at Berry Plastics, says the "financial aspects" were key to the deal to award Symantec a three-year contact for its Endpoint Protection product for around 6,000 desktops. Although there were technical considerations, too, such as Symantec's desktop security utilizing less storage space for antimalware DAT files. Symantec made the deal very appealing financially, Mers says.
Despite such victories for Symantec, McAfee, the No. 2 player in the security software market, recently reported a 38% rise in second quarter earnings and increased revenue, thanks in large part to sales help from business partners.
McAfee's big push of late has been security for smartphones, including the iPhone and Android-based devices, whether in the hands of the consumer or the business person.
To that end, McAfee recently acquired mobile-device management vendor Trust Digital, used in the enterprise, and Singapore-based tenCube in the consumer area. Symantec's approach so far has been to develop software in-house, including its Mobile Management product introduced last November, according to Khoi Nguyen, group product manager in Symantec's mobile security group.
Today, McAfee generates 85% of its security software revenue through sales channels, says Alex Thurber, vice president of worldwide channels at the company. "We have 20,000 partners -- 1,000 of them really invested in us," he notes, citing SHI, InSight, Dell, CDW, AT&T, Verizon, Brocade and HP. "Asia-Pacific has been our fastest growing market."
HP also wants to dig into the security software market, and just announced its intent to acquire software vulnerability company Fortify Software, a longtime partner.
Plans include combining the vulnerability-scanning capabilities HP gained through the SPI Dynamics acquisition with the static analysis in Fortify's product to offer a comprehensive security assessment product for the enterprise, says Mark Sarbiewsi, vice president products for HP Software and Solutions.
HP's appetite for security and IT management buyouts has been hearty, with the company acquiring over the past five years Peregrine Systems, Mercury Interactive and intrusion-prevention systems appliance vendor TippingPoint, which closed this April. But Gartner analyst Ruggero Contu says HP doesn't count as a player of significance in the software security market in terms of market share, with just $2.4 million in 2009, down from $15.1 million in 2008.
Where HP does have a presence is in its security services arm gained through its acquisition of EDS in 2008 for over $13 billion going up directly against IBM. Now known as HP Enterprise Services, the division earlier this year announced security-services packages including a line of third-party security and compliance offerings.
While Symantec, McAfee and IBM have grown through acquisitions of smaller security vendors, and now McAfee is going to be acquired by Intel, enterprise customers will be bracing for yet more change.
Takeovers of smaller companies are not always viewed as a positive thing by enterprise IT managers.
Mark Starry, director of infrastructure and security at Capital Region Healthcare based in New Hampshire, was not overcome with joy when he learned last month that IBM was acquiring his patch management vendor, BigFix.
Too often Starry has seen acquiring companies neglect software development or otherwise muddy things. But the management at both IBM and BigFix have assuaged his concerns somewhat, Starry says, because they say BigFix will be left as a stand-alone group. "Maybe they'll even give them resources to speed up software development," he says.
http://www.networkworld.com/cgi-bin/mailto/x.cgi?pagetosend=/news/2010/081910-security-software-industry-growing.html&pagename=/news/2010/081910-security-software-industry-growing.html&pageurl=http://www.networkworld.com/news/2010/081910-security-software-industry-growing.html&site=security
|
| Back to top |
|
|
| |
| When it comes to emerging platforms like smartphones, tablets, and embedded networked systems, the old model of separate antivirus security companies is officially dead. And Intel's purchase of McAfee puts a stake in it. The PC model simply wasn't sustainable because it put security companies at odds with the platform providers they secured, and the solutions were an ugly trade-off of solving some potential security exposures by causing consistent performance problems. Intel's move to buy McAfee, much like Microsoft's purchase of Sybari years ago, is an indicator of change that will felt as the next generation of technology is developed for the market.
The reason Microsoft decided to let third parties do security on Windows was that, initially, its entire model was based on a heavy third-party application plan. In addition, security initially was mostly about access, and given that computers generally weren't networked, viruses that spread via floppy drives were relatively easy to manage. So Microsoft left it up to others, and an industry of the likes of McAfee, Symantec, and Trend Micro was born.
But so was a big problem. You can't sell security to a secure customer: You have to make them feel insecure. This is called the insurance sale; you have to make people think they are going to have a loss if you want them to buy something that will compensate them for it. If folks feel safe, then they won't buy.
This put security vendors, particularly AV vendors on Windows, at odds with Microsoft because they increasingly had to find and point out flaws in Windows in order to sell products that mitigated these flaws.
The process to both intercept and scan for viruses remains resource-intensive. Until there was performance headroom in the past decade, a virus scan could bring a PC to its knees; users either turned the process off or complained about the poor performance. This became particularly painful as Apple improved and users had a choice, and increasingly chose, the platform that didn't have antivirus software.
Smartphone, tablet, and embedded vendors certainly don't want to repeat this mistake, and Intel is offering them an alternative by buying McAfee.
This won't happen overnight, nor will it be easy, but Intel's plan is to recognize that security exposures are not only going to get worse, but they also will spread to other systems that are increasingly being connected. Monitoring, communications, automotive, medical, manufacturing, in-flight, and law enforcement systems (and this is hardly an exhaustive list) are being connected to the network, and that connection becomes vulnerable to attack by viruses and hackers. However, the companies building and selling these systems generally have no competence with this kind of problem because their systems have either not been connected, or they used dedicated and secured networks and not the Internet.
This could lead to unimagined exposures that either could significantly slow products to market or cause them to fail spectacularly once they arrive. Even the new smartphone and emerging smartphone-based tablet space -- which is designed to be networked -- is largely driven by vendors that haven't really had to worry about viruses and hackers except when it comes to breaking the carrier lock on the devices. Even for that relatively simple exposure, they have had a troubled history.
This suggests a different approach: one in which security is designed in at the front-end of a product. Intel now has a plan for those vendors that don't have the expertise to do this.
Intel's purchase of McAfee makes sense because you need a team that has expertse in the threat in order to deal with it in a timely way; the PC market is where the expertise exists. Symantec was too broad and expensive, firms like Kaspersky too limited and likely too remote physically, and McAfee appeared to be a bargain. So a marriage was conceived.
Because Intel doesn't yet have a software competence, it is at least initially leaving the firm separate, but I expect it will eventually revisit this as it discovers the need to combine the companies' acquired software competencies into a more cohesive unit. The goal, however, is to create an environment in which security is designed in from the start, with hardware tuned for it and performance impact, minimized.
This path is not without risk: Intel is neither a software nor security expert at this point, and acquisitions often challenge firms as they learn to understand them. However, without an edge, Intel likely wouldn't be able to make much inroads into the targeted markets, and performance alone isn't enough edge. Security in an insecure world could be just the edge to get it into consideration and to design wins once the solution is fully fleshed out.
That makes this one of the few high-risk strategic decisions this year -- and large stable companies like Intel aren't typically known for that. That's why large, stable companies often don't stay large and stable. More of them should take regular bets to better assure their long-term future. Intel did, and suddenly it isn't just big -- it's also interesting again.
-- Rob Enderle is president and founder of Enderle Group. Special to Dark Reading.
http://www.darkreading.com/blog/archives/2010/08/intel_buys_mcaf.html;jsessionid=GBZEEEOF3XGJNQE1GHPSKHWATMY32JVN |
| Back to top |
|
|
| |
| Editor's note: Allan Krans is a senior analyst with Technology Business Research. Chip giant Intel Corporation (Nasdaq: INTC) is acquiring security firm McAfee (NYSE: MFE) in an all-cash deal worth nearly $7.7 billion. Krans analyzes the deal. HAMPTON, N.H. – While dwarfed by market leader Symantec, McAfee enjoyed the differentiation provided by being the largest pureplay security vendor. Its positioning was that as Symantec worked to balance both security and systems management, its sole focus was on improving and expanding its presence in the security space. After riding its pureplay status and frequent acquisitions to close the gap in security, McAfee now joins Symantec in providing security as part of a much broader product set.
During 2Q10 McAfee ended a growth streak that included seventeen consecutive quarters of double-digit revenue growth largely fueled by acquisitions. McAfee will hand the title of largest pureplay security vendor to Trend Micro in return for the multiple benefits of joining a much larger organization including revenue stability, ability to increase cross-selling, product integration, and access to greater financial resources.
McAfee secures its ride higher in the supply chain
In the consumer and SMB markets, security software distribution relies heavily on hardware-based partnerships. PC OEM agreements with leading PC vendors are highly sought after due to the massive scale of customers security vendors can access. The year-long lead up to the extension of Symantec's OEM deal with HP illustrates just how important hardware agreements are for distribution security software.
Instead of dealing with the PC OEMs themselves, McAfee now sits up a level in the hardware supply chain and has the ability to embed its security software in processor components before they are used by the actual PC OEMs such as HP, Dell, Lenovo, and others.
Distribution channels tip the scales in favor of success
Owning a distribution channel has powerful influence over the ultimate success or failure of acquisitions. Intel's firmly engrained position across all IT hardware, from PCs to mobile phones provides a powerful advantage in turning the purchase of McAfee into a net benefit. EMC's acquisition of RSA is a good example of this effect, as EMC was able to leverage its leading position in storage hardware to both integrate and cross-sell RSA into its customer base.
On the other hand, Symantec's acquisition of VERITAS illustrates some of the difficulties that can arise when a company largely relies on hardware partners rather than ownership for distribution. Symantec's Storage and Systems management business is competing in a market dominated by vendors like EMC, IBM, and HP, which use hardware platforms as a vehicle for management software sales.
Intel can prove security belongs on mobile chips
In a market still dominated by desktops and laptops, the business model for embedding software at the processor level is still immature. The prevalent model is to load software on a finished product, a model that does not give much advantage to a Intel/McAfee combination. However, with the rise of tablets and mobile phone-based computing will bring with it increased demand for software intelligence that is embedded at the hardware level. All security vendors have recognized and responded in some way to the mobile computing security threat, but offerings are not currently prevalent in the market.
With more sensitive and even confidential computing tasks being performed on mobile devices, demand for security will not lag far behind. Intel's acquisition of McAfee may not have a profound impact in the PC market, but could allow both Intel and McAfee to benefit significantly from rising demand for embedded mobile security that has a minimal impact on device performance.
Get the latest news alerts: Follow LTW at Twitter.
http://localtechwire.com/business/local_tech_wire/news/blogpost/8161574/ |
| Back to top |
|
|
| |
| SAN FRANCISCO (Dow Jones)--Intel Corp. (INTC)'s $7.7 billion bid for McAfee Inc. (MFE) highlights the growing importance of mobile security, a field that is expanding rapidly as handheld devices become more important to both consumer and business users.
On Thursday, the Santa Clara, Calif.-based chip giant said it will pay $48 for each share of McAfee, a 60% premium to Wednesday's closing price. The deal will help Intel incorporate McAfee security products into its chips. The deal comes as computing moves away from desktops amid the growth of wireless Internet access, which creates new security threats for users as well as opportunities for security providers. In March, data tracker IDC forecast world-wide mobile-security license and maintenance revenue would more than double to $2.7 billion by 2014 from $1.3 billion in 2009.
The Intel-McAfee deal, as well as the explosion of threats, may rekindle interest U.S. publicly traded security companies, like Symantec Corp. (SYMC) and Websense Inc. (WBSN). It may also pique interest in overseas security companies, such as Japan's Trend Micro Inc. (4704.TO), Finland's F-Secure Oyj (FSC1V.HE), as well as privately held companies like Spain's Panda Security and Russia's Kaspersky Lab.
"This deal opens the eyes of investors to the value of the security market, which over the past year has been out of favor," said Daniel Ives, a senior analyst with FBR Capital Markets & Co. in New York.
Investors quickly reacted to the deal, bidding up shares of McAfee competitors that might now be on the radar screens of potential partners or buyers. In late afternoon trading, Symantec shares were up 6.7% at $13.45, while Websense Inc. was up 5.2% at 19.40.
"Maybe some of Intel's competitors need to have tighter relationship with security companies to emulate what Intel is doing," said Steve Ashley, an analyst at Robert W. Baird.
Like McAfee, Mountain View, Calif.-based Symantec has rushed to be part of the mobile security landscape. In May, Symantec unveiled Norton Everywhere, a family of products targeted primarily mobile devices. It also made an undisclosed investment in Mocana Corp., a venture-backed San Francisco start-up that specializes in mobile security.
Other firms have done the same. Kaspersky Mobile Security 9, from Moscow-based Kaspersky Lab, protects consumer smartphones from data loss, viruses and spam, while Tokyo-based Trend Micro offers two products for protecting mobile phones, one for consumers and one for companies.
-By Jeanette Borzo, Dow Jones Newswires; 415 765 8230; jeanette.borzo@dowjones.com [ 08-19-10 1554ET ] |
| Back to top |
|
|
| |
| Intel will acquire security software tools supplier McAfee Inc. for $7.68 billion in cash, the company said today. The boards of both companies have agreed to the blockbuster deal, which Intel said will enable it to provide processor and network-based security. The deal puts a 60 percent premium on McAfee's share closing price yesterday, and underscore's Intel's desire to further expand beyond its core hardware business. Intel said it will operate McAfee as a wholly-owned subsidiary that will report to the company's Software and Services Group.
Intel said it has placed security at the same level of priority strategically as improving energy efficiency and providing Internet connectivity.
"With the rapid expansion of growth across a vast array of Internet-connected devices, more and more of the elements of our lives have moved online," said Paul Otellini, Intel's president and CEO, in a statement. "In the past, energy-efficient performance and connectivity have defined computing requirements. Looking forward, security will join those as a third pillar of what people demand from all computing experiences."
McAfee has a broad portfolio of products that are designed to provide security for devices ranging from smart-phones to PCs to core enterprise systems. Among its core competitors are Symantec, CA Technologies, IBM, Microsoft and Trend Micro.
"The cyber threat landscape has changed dramatically over the past few years, with millions of new threats appearing every month," said Dave DeWalt, McAfee's president and CEO, in a statement. "We believe this acquisition will result in our ability to deliver a safer, more secure and trusted Internet-enabled device experience."
The deal will close pending shareholder and regulatory approval.
About the Author
Jeffrey Schwartz is executive editor of Redmond Channel Partner and an editor-at-large at Redmond magazine.
http://reddevnews.com/articles/2010/08/19/intel-to-acquire-mcafee.aspx |
| Back to top |
|
|
| |
| Demand for security is on the rise, as computing devices become increasingly mobile and connected. According to Technology Business Research, expects Intel to quickly move to embed McAfee technology into all of its device platforms, providing a stronger baseline of security. The addition of McAfee will differentiate Intel's platforms from competitive offerings by Advanced Micro Devices as well as ARM. Going forward, Intel wants IT managers and consumers to associate McAfee, security and Intel. TBR believes Intel ultimately views its planned acquisition of McAfee as a means of continuing growth by adding hardware-based security to its numerous platforms for PCs, embedded devices and, increasingly, mobile devices. Through the acquisition Intel will position security as the "third pillar" of its device platforms, following energy efficient performance and Internet connectivity.
Intel's acquisition of McAfee will also change the landscape for security software. While dwarfed by market leader Symantec, McAfee enjoyed the differentiation provided by being the largest pure-play security vendor. Whereas Symantec worked to balance both security and systems management, McAfee's sole focus was on improving and expanding its presence in the security space. After riding its pure-play status and frequent acquisitions to close the gap in security, McAfee now joins Symantec in providing security as part of a much broader product set. McAfee will hand the title of largest pure-play security vendor to Trend Micro in return for the multiple benefits of joining a much larger organization, including revenue stability, the ability to increase cross-selling, product integration and access to greater financial resources. McAfee will continue to sell and support its current product lineup under Intel.
More recently, Intel has begun internally leveraging software to augment its platforms, following the belief that today's platforms require both software and hardware. To that end, Intel has made software a vital piece of its efforts to win in the tablet and handheld devices space. The company has partnered with Nokia to spur development of the MeeGo operating system and created the Intel AppUP application store.
According to TBR, Intel's immediate goals are to better protect device users in tasks such as social networking, e-commerce and online productivity. TBR believes Intel and McAfee are likely to benefit significantly from rising demand for embedded mobile security that has a minimal impact on device performance; however, TBR believes Intel will continue to focus on selling silicon. Therefore, the chipmaker hopes the integration
TBR believes that the rise of sensitive computing tasks performed on mobile devices will cause demand for security to continue to grow. Although Intel's acquisition of McAfee may not have an immediate impact on the PC market, we expect the tie-up to change the dynamic of hardware-software partnerships.
TBR claims the agreement with McAfee will pave the way for additional embedded software agreements, creating a new distribution channel with powerful influence over the ultimate success or failure of software makers, based on their ability to partner with vendors like EMC, IBM and HP, which use hardware platforms as vehicles for software sales.
However, the developments will not fully take effect until approximately 2012, when Intel begins integrating McAfee directly into its hardware. The companies have been working together for 18 months and will release joint products in 2011; however, TBR does not expect the first fully-embedded security platforms to arrive until 2012.
http://www.xbitlabs.com/news/other/display/20100820101907_Intel_s_Platforms_to_Get_Advanced_Security_Thanks_to_McAfee_Acquisition.html
|
| Back to top |
|
|
| |
| Computerworld - Several security analysts today expressed surprise that Intel would purchase security tool maker McAfee, noting that at first glance the move makes little sense for a pure hardware firm. Intel Thursday agreed to buy McAfee for $7.68 billion, which analysts are calling a premium price tag.
"I'm baffled," said Peter Firstbrook an analyst with Gartner in Stamford, Conn. "I don't see any synergy at all between McAfee and Intel."
At best, he added, the acquisition could be a good venture capital investment for Intel. "And they may get a little cross R&D benefit from the deal as well," he said,
In fact, analysts said, the deal could prove beneficial to McAfee rivals like Symantec, Sophos and Trend Micro, at least in the short term. Each can be expected to move quickly to try and take advantage of a distracted McAfee prior to the deal's closing and during the integration phase, they said. "McAfee is going to be a little bit distracted for sure. It's probably good news for Symantec," and the other vendors, said Firstbrook.
Intel president and CEO Paul Otellini, said this morning that the acquisition was driven by Intel's belief that security has become a fundamental component of online computing.
"With the rapid expansion of growth across a vast array of Internet-connected devices, more and more of the elements of our lives have moved online," he said in a statement, adding that McASfee will bring to his firm "incredibly talented people with a track record of delivering security innovations, products and services ... [that are used to make] the Internet safer and more secure."
Intel said that McAfee will be a wholly owned subsidiary of Intel reporting into the Software and Services Group.
Firstbrook predicted that efforts to integrate McAfee's security technology into Intel hardware platforms will likely be a time consuming process, and noted that it could have been achieved more chickly and cheaply by simply partnering with security companies.
"It's a different product, it's a different market, it's a different customer base," Firstbrook said. "Intel moves in terms of quarters and years. McAfee has to move daily in terms of responding to [security] threats. One operates much higher in the stack. The other is much lower in the stack."
McAfee's enterprise customers are likely a bit puzzled by the move, said Andrew Jacquith, an analyst at Forrester Research in Cambridge, Mass.
"McAfee customers in many cases have reasons to be worried, and not just because of this deal," he said, noting that many users are already upset with McAfee over a flawed security update that crippled thousands of corporate PCs.
"In the wake of McAfee's DAT issue many customers were already looking for other suppliers," he said. Uncertainty over Intel's plans for McAfee "may accelerate that trend," he said.
Intel's purchase, though puzzling to the analyst community, is not the first time that a hardware company has purchased a security vendor.
For instance EMC purchased RSA in 2006, and IBM has gained security tools from Rational, Ounce Labs and WatchFire in recent years, Just this week, Hewlett-Packard said it had purchased Fortify, an application security vendor, for an undisclosed amount.
Pete Lindstrom, an analyst with Spire Security in Malvern, Pa., did say that the deal could help Intel diversify its business over the long term. "Intel is a big company flush with cash looking for ways to diversify. It's no secret Intel is interested in services, and McAfee has some interesting security services in the cloud," he said.
Jaikumar Vijayan covers data security and privacy issues, financial services security and e-voting for Computerworld.
http://www.computerworld.com/s/article/9180942/Intel_McAfee_deal_baffles_security_analysts?taxonomyId=17 |
| Back to top |
|
|
| |
| News crossed the wires this morning that chip maker Intel is buying McAfee for $8 billion in cash and stock, ending one of the most anticipated corporate acquisition watches in Silicon Valley history. The surprise is that McAfee's suitor is Intel. For past two years, rumors and speculation have run wild that McAfee was seeking a sale to a larger company. The best guess for McAfee's new home was Hewlett-Packard, where it would complement its services and hardware portfolios, or Microsoft, where it would bolster its ongoing security efforts.
Intel swooping in and defying conventional wisdom potentially points to something bigger: embedded security beneath the operating system. Intel has been investing in software applications and tools that reside in silicon, which is especially significant for the development and improvement of mobile devices. In theory, McAfee could provide a layer of security that Intel will need in its firmware stack.
Is this a game changer? Perhaps. But it will take a lot of technical integration and development to make this work.
What can McAfee solution providers expect under Intel ownership? In the short term, not much. Undoubtedly, the channel leadership - Alex Thurber for global and Fernando Quintero for the Americas - will come out with reassuring statements that it's business as usual for the time being. McAfee is planning to host a partner summit at its annual Vision conference in Las Vegas. Given that former President Bill Clinton is the marquee speaker, the show will likely go on as scheduled.
In terms of the security landscape, this definitely reshapes it. Trend Micro is now the king of the pure-play security vendors in terms of revenue, followed closely by Check Point Software Technologies. While perceivably good news for them, Intel buying out McAfee will likely renew debate whether pure-play security companies can remain viable in the long term.
My observation is that pure-play security companies tap out at roughly $2.5 billion in top line revenue. It was around that mark that Symantec bought Veritas and diversified into storage management. McAfee is roughly $2.6 billion. While CEO Dave DeWalt promised to make one acquisition per quarter to bolster growth, there were no security companies left to buy to significantly move the needle.
So far, Wall Street is giving mixed reviews to the deal. Intel's stock is down, while McAfee's stock is up. This is an emerging story, and Intel and McAfee have many questions to answer - particularly to their channel partners. More to come …
http://blogs.channelinsider.com/secure_channel/content/security_business/surprise_intel_buys_mcafee_for_8_billion.html |
| Back to top |
|
|
| |
| Intel's intended acquisition of McAfee for $7.68 billion is a real head-scratcher. They could have purchased comparable security technology or more attractive security businesses for much less. I don't get it, and I want to get it because I am impressed by Intel's leadership efforts with security and McAfee's pragmatic approach to endpoint security. This deal just does not make sense on so many levels, except for McAfee shareholders who were last seen in the streets hugging and giggling. Still, Intel is full of smart people and there are ways that McAfee capabilities can contribute to the bottom line. These are some of the capabilities that may be interesting to follow:
* Creates demand for more powerful processors with embedded security. Nothing consumes processor cycles like AV-based endpoint security, and the complexity of inspecting content for malware is only going to increase. Perhaps McAfee on a chip will increase sales in Intel's core business. Ok, that's a stretch - this is not like EMC securing its core storage business with RSA or Oracle controlling its database environment with Sun hardware.
* Intel can build on the skills required to distribute huge volumes of attack signatures from internal data centers through the cloud to remote endpoints. The cloud is changing distribution models allowing vendors to reach customers directly, and some of the traditional middle-man approaches will have to evolve to avoid being tomorrow's losers. If Intel does not want to be totally dependent on platform vendors (e.g. Dell, HP), operating system vendors (e.g. Microsoft), or service providers (e.g. AT&T, Verizon) to ship software products and upgrades to consumers, then it needs to own that competency. McAfee is excellent at automated world-wide delivery of anti-virus data from high performance data centers to a large number of consumers. Of course, for less money Intel could discover that Lumension also has outstanding communication capabilities for managing patches and configuration information as do a gazillion other less expensive AV vendors.
* Intel can accelerate adoption of security features in hardware by being the first to offer products. vPro has exciting security features for isolating virtual machines, managing security keys and secrets, and updating security profiles even if the machine is hibernating. However, the security industry has been glacially slow in taking advantage of these features- partly because it raises "innovator's dilemma" problems that are not clearly in the security vendors' best interests. There is no question that McAfee brings considerable security expertise, and that McAfee has been actively working with Intel so this acquisition may add needed momentum to Intel's security program. The downside is that deep-dive conversations with security businesses such as Microsoft, Symantec, and Trend Micro will be more difficult knowing that secrets may find their way quickly to a competitor, and it is not at all obvious that McAfee's traditional endpoint security is the type of security that is best for Intel.
* Intel diversifies its business to better ride out tough economies by branching into endpoint security software. Intel chip production and revenues drop off dramatically when orders for desktops and laptops dry up while security has performed well during this world wide recession. Buying an established and stable billion dollar business provides Intel more flexibility in managing its business and hopefully smoothing out disruptions caused by economic cycles.
But if the idea is to diversify with security lines of business, leverage unique technology, or establish a cloud-based infrastructure that can directly reach consumers, is McAfee really the best choice? Just for fun, if I had several billion dollars to buy a present for Intel, I would suggest these billion dollar a year businesses:
1. Check Point offers a strong sustaining network appliance business and also has Zone Labs endpoint security expertise. Intel chips can drive Check Point firewalls (albeit in numbers that may not interest Intel), Check Point's software blade architecture could provide Intel with great flexibility in incorporating future growth opportunities, and Zone's endpoint security with DLP can be used to enhance hardware security.
2. Citrix core application virtualization business would deliver annual revenues while its Xen virtualization technology could open paths for Intel into storage systems, networking features, endpoint security and management, and cloud-based delivery systems. In fact, a bare metal hypervisor embedded with Intel Inside could be a disruptive force to the way software is secured and deployed.
3. Trend Micro, if Intel must do endpoint security, has a significant head start in using virtualization and cloud-computing while also offering top-tier endpoint security. Compared to other security vendors, Trend is ahead of the curve when it comes to using the cloud to protect consumer configurations and business data with a business model that would be attractive to Intel. That seems to be a better fit than McAfee.
Who else makes sense for Intel? Should they act like Cisco and focus on buying smaller companies with interesting technology? Should they look for mature business with predictable revenue streams like Symantec? Or is acquiring McAfee a match made in heaven? Who would you buy if you were Intel? Hey, it's only money!
http://blogs.computerworld.com/16790/intels_purchase_of_mcafee_is_a_head_scratcher |
| Back to top |
|
|
| |
| Trend Micro's position is that "Intel's resources may now enable McAfee to offer protection to multiple devices and endpoints, replicating what other vendors, such as Trend Micro, have already achieved through Smart Protection Network." Trend sees Intel's acquisition as "a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products", but goes on to warn that "the embedded-software model is fundamentally different from the security-software operating model and this is a good opportunity for customers to review their relationship with their security partner to assess whether they will be receiving the services and expertise they need."
- - -
Everyone's talking about Intel's agreement to acquire McAfee as a wholly owned subsidiary. At $7.68 billion it's definitely a big deal, but what will it mean to the rest of the security industry? I asked various security companies for their take on the event.
Effects in the Enterprise
Alex Eckelberry, president and chief executive of McAfee competitor Sunbelt Software, responded immediately and at length. "I think this is a smart move for Intel", said Eckelberry. "They have been playing at the edge of antivirus for years, but now this gives them a real footprint in the market."
Eckelberry sees work ahead in the mobile security market. "I think Intel's stated interest in leveraging McAfee's technology to go after the mobile and cloud markets will not be without challenges. With five major platforms out there (Symbian, Blackberry, Droid, iPhone and Windows Phone), there is quite a bit of work to be done to support a broad range of mobile platforms. "
There may also be some challenges as far as corporate culture goes. "McAfee is a fairly large company, but Intel is a behemoth," Eckelberry said. "Nevertheless, they share similar Silicon Valley roots and there should be an easier integration than past acquisitions such as LANdesk, which Intel ultimately spun out after having had similar high hopes as they do with McAfee now."
Consumers won't be affected much, at least initially, suggested Eckelberry. "If Intel lets McAfee have its freedom as an independent subsidiary, I wouldn't see much of an impact." On the other hand, Eckelberry said he sees a shakeup at the enterprise level. "All the enterprise-oriented AV companies will look for any weakness in McAfee and go after existing customers. Sophos, Trend Micro, Symantec and Sunbelt are the only companies that have the technology to compete with McAfee. To say that enterprise antivirus is competitive is a great understatement – it is one of the most competitive segments in technology. And there will be fallout in the acquisition, there always is. Competitors will smell blood."
Heightened Attention Good for All
Several vendors expressed a very positive reaction to the acquisition, on the basis that the attention from Intel is a boon for the entire security industry. Steve Orenberg, president of Kaspersky Lab Americas, observed "The acquisition of McAfee by Intel is a strategic step forward for both companies. From Kaspersky Lab's side, we can state that it is very positive news for the market as it reinforces the fact that IT security is among the most important issues for both the B2B and B2C sectors. Now that one of the key hardware producers has added a new direction to its business by acquiring a major player in the IT security market, it is obvious that this will create more competition and drive the industry to grow more rapidly, and that is always a positive thing for the rest of the players involved."
Expressing similar sentiments, Juan Santana, CEO of Panda Security, said the acquisition "is an unexpected move that highlights the importance of security going forward. In a world where most appliances and gadgets that consumers use have some kind of internet connectivity, security becomes a differentiator. Intel has seen this and they have taken a step forward to be well positioned for that. Computer security cannot be ignored and this move highlights once again the need for it to be top of mind for consumers. We expect no changes in the offering to consumers as a result of the transaction."
Check Point Software's official position is that the acquisition "is good news for security, showing … the importance of security on the corporate agenda. Check Point doesn't expect this to impact our business, since McAfee isn't a major competitor in network security, where we have been the leader for more than 17 years." The company went on to note that "Check Point is now the largest vendor solely focused on security, and we remain dedicated to helping the tens of thousands of customers we serve today across 100% of the Fortune 100."
Microsoft offered this terse statement on the subject: "We look forward to continued partnerships with McAfee, Intel and the rest of the industry to help protect customers from today's ever evolving threat landscape."
Securing the Hardware
I don't normally cover mobile-specific security products, and thus haven't worked directly with Lookout Mobile Security. But their CEO and co-founder John Hering was enthusiastic. "Intel's acquisition of McAfee signals to the industry that smartphones and other connected devices are joining the web of devices we trust with critical data and that these devices need to be protected," said Hering. "We have seen threats rising across the major mobile platforms and expect this trend to increase as mobile devices continue to become the dominant computing platform."
Trend Micro's position is that "Intel's resources may now enable McAfee to offer protection to multiple devices and endpoints, replicating what other vendors, such as Trend Micro, have already achieved through Smart Protection Network." Trend sees Intel's acquisition as "a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products", but goes on to warn that "the embedded-software model is fundamentally different from the security-software operating model and this is a good opportunity for customers to review their relationship with their security partner to assess whether they will be receiving the services and expertise they need."
Securing the User
A Symantec spokesperson agreed with others that the acquisition directs helpful attention to the importance of security. "Symantec has been uniquely focused on delivering end-to-end, comprehensive protection to secure and manage information and identities in a connected world. Today's announcement by Intel to acquire McAfee emphasizes the growing relevance and need for security protection that extends beyond the PC and further reflects Symantec's ongoing strategy."
Symantec aims to protect the user, not the specific device. "Symantec believes it is important to focus security in the future on people and the information they need to access, independent of the device they may be using. That will require security to work seamlessly across multiple platforms as users switch devices to use, store and transmit information. Symantec's strategy is focused on providing a broad portfolio of protection that … provides security protection anytime, anywhere and on any device."
Vitor Souza, BitDefender's Global Communication Manager, isn't worried. "BitDefender customers are not affected in anyway because business goes on. McAfee already had very strong OEM deal so their core strategy was always combination of hardware and security. It will be interesting to see how they will manage R&D for the 'new McAfee'. It has been a while since McAfee put out a competitive product in the market."
McAfee's competitors in the security realm have a positive outlook about Intel's re-entry into the field. They don't anticipate big changes for their users; rather, they see Intel's attention as beneficial to the security industry as a whole. If McIntel just continues with business as usual, that makes perfect sense. But if they actually break new ground with hardware-supported security, all bets are off. We'll know next year.
http://www.pcmag.com/article2/0,2817,2368056,00.asp
|
| Back to top |
|
|
| |
| Instead of quaking in their boots about Intel's acquisition of McAfee, security software companies have said the move is positive for the market. As part of the acquisition, which cost Intel $7.68 billion, Intel will fold McAfee into its software unit and says the reason it has bought the company is because security is a fundamental part of online computing, something that other security vendors agree with.
Although Kaspersky said it didn't normally comment on competitor ventures, it described the venture as "positive news for the market," adding that it reinforces the fact that IT security is "among the most important issues for both the B2B and B2C sectors".
Trend Micro added that the decision was "a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products."
Panda Securities two pence is that the buy "is clearly elevating the importance of IT security to new heights within the computing industry."
The McAfee deal is Intel's biggest acquisition since it bought Level One Communications for $2.2bn in 1999 and follows a flurry of consolidation activity in the technology sector, including Hewlett-Packard's acquisition of Palm, the smartphone maker; and software manufacturer Oracle's $7.4bn purchase of computer hardware group Sun Microsystems.
Intel said that the acquisition would incorporate security concerns into computers, mobile phones and cash machines.
Although security vendors believe this will help drive the traditional security market, some, including Sophos and Trend Micro are a bit wary of Intel's big change claims.
Kaspersky told TechEye: "Now that one of the key hardware producers has added a new direction to its business by acquiring a major player in the IT security market, it is obvious that this will create more competition and drive the industry to grow more rapidly, and that is always a positive thing for the rest of the players involved."
Eva Chen, Trend Micro's CEO and co-founder agrees: "Intel's decision to purchase a security software company is a clear statement to the industry and investors that security is absolutely fundamental to future technology services and products. For current and future customers, Intel's resources may now enable McAfee to offer protection to multiple devices and endpoints, replicating what other vendors have already achieved.
However, the company warned that the embedded-software model is fundamentally different from the security-software operating model. It advised customers to "review their relationship with their security partner to assess whether they will be receiving the services and expertise they need."
British insecurity outfit Sophos also had some reservations. Graham Cluley, senior technology consultant at the security company, told us that although he believed that the Intel/McAfee deal reinforced the view that the security industry is an attractive growing market for investors, he warned that: "infrastructure vendors acquiring security vendors is not guaranteed to succeed.
"Security - given the unique nature of volume and changing nature of threats, compliances, new models - requires a dedicated focus.
"And if Intel's acquisition of McAfee is designed to help it focus on embedding security into consumer-orientated hardware (phones, ATMs, devices etc.), it will be a major distraction from their enterprise business, and could shift it away from servicing the needs of enterprise customers.
"It's also worth bearing in mind that we're seeing more and more threats taking place in the internet (think recent social networking attacks on sites like Facebook) rather than close to the CPU. In these increasingly common attacks, chip-based security will not offer any advantages."
Symantec remained an ally to the chip giant. When we asked how it felt about competing with the giant a spokesperson told us: "Symantec and Intel have maintained a strong relationship for many years. Our joint strategic alliance runs across many areas including manageability, security, endpoint virtualisation and data protection and the majority of the initiatives we have going with Intel today are not specific to security or other technology that is competitive with McAfee. As such, we anticipate that Symantec and Intel will continue maintain a strategic relationship and work together on these fronts."
Intel's acquisition of McAfee still requires the approval of McAfee shareholders and regulatory clearance.
http://www.techeye.net/business/security-vendors-respond-to-intels-mcafee-buyout |
| Back to top |
|
|
| |
| NEW YORK (CNNMoney.com) -- Intel's $7.7 billion purchase of security company McAfee makes plenty of financial sense, but it's a head-scratcher from a technology standpoint. The deal seemed to come out of the blue: Intel is the world's largest chipmaker, so a security software company wouldn't seem to be a good fit for the hardware-focused vendor. Intel has previously stated that security is one of its top priorities as it tries to get its processors into every type of connected device. But existing relationships with security companies, including McAfee, appeared to many analysts to be sufficient for Intel to execute on its technology goals.
"I'm not quite sure why they bought this company," said Steve Kleynhans, microprocessors analyst at Gartner. "The purchase plays to all of Intel's initiatives, but the question remains: Did it have to buy a company to do that?"
A call between Intel executives and investors Thursday morning did little to answer that question. Intel's leaders went buzzword crazy in describing the deal, saying over and over that the McAfee purchase offered "deeper collaboration and integration between hardware and software," "substantial differentiation for our products and platforms," and "enhanced security products."
But Intel CEO Paul Otellini offered up one buzz phrase that actually means something to the company right now: "Value for Intel shareholders."
Intel has $17.8 billion cash on hand, which is just sitting there, earning very little for the company's shareholders.
So what to do with that cash? Intel could increase its dividend, but there's only so much it wants to give away. It could invest in the businesses it already owns, but the company was recently downgraded by analysts because of slowing demand for personal computers -- a problem that cuts right to the core of Intel's business model.
Alternatively, Intel could buy a company that it thinks will generate income for its investors. As Berkshire Hathaway CEO Warren Buffett said about his surprise move to acquire the Burlington Northern railroad company last year, it was an opportunity to deploy "cash in a business we understood and liked for the long term."
The question is: Did Intel make the right deal?
Many analysts expressed concern that Intel paid a 60% premium over McAfee's closing share price on Wednesday, which is expensive by most standards. But others noted that the return on Intel's investment will likely far exceed what it paid for the security company.
"Everyone's focusing on how expensive it was, but with this deal, Intel's cash flow is growing, its balance sheet stays clean, and the capital is at a very low cost," said Ken Hackel, president of CreditTrends.com and author of Security Valuation and Risk Analysis. "This gives Intel a positive spread over what it'd earn ordinarily by investing in the slowing PC market or holding onto its cash."
Hackel estimated that Intel's total cost of capital on the McAfee purchase would be about 4%, but the cash return on its invested capital would probably be around 8%.
Software in general is a much higher-margin business than hardware, and McAfee is no exception, with a gross margin near 75%. Intel's is around 55%.
So if it's going to go after a security company, Intel likely picked up the best one it could get. Symantec has a larger share of the market than McAfee, but Symantec (SYMC, Fortune 500) is a significantly larger company and would be harder for Intel to integrate. Trend Micro was another option, but its market share is slipping. Other players' offerings are mostly tailored for large corporate customers.
"McAfee was the right one to buy," said James Ragan, an analyst at Crowell, Weedon & Co. "It competes very well with Symantec, and it gives them a big company that's not too big and has a strong mix of corporate and consumer offerings."
But some analysts who praised the move from a financial standpoint criticized it from a 30,000-foot view.
Intel will have to figure out how to integrate a big software company into its hardware business -- and it will have to address the concerns of its existing clients who use products made by McAfee competitors.
"I would highly suspect that the cost of capital is one of the reasons for this acquisition," said Erik Suppiger, a senior research analyst at Signal Hill Capital. "But it's not a good business decision if it's not going to execute well."
Shares of McAfee (MFE) soared 57% on Thursday, while Intel's (INTC, Fortune 500) fell more than 3%.
http://money.cnn.com/2010/08/19/technology/intel_mcafee_deal/index.htm?section=money_latest
|
| Back to top |
|
|
| |
| If Intel's bombshell bid last week to buy McAfee for $7.68 billion pans out, the companies pledge to bring an unprecedented level of embedded security to networked devices ranging from smartphones to servers, potentially changing the way in which security is delivered to enterprise IT shops. Tech industry's M&As in 2010
Intel and McAfee have been working closely on a host of projects for 18 months and expect to show the first fruits of their labor early next year. Among other things, McAfee technology could complement Intel's existing hardware-based security and management technology, dubbed vPro.
While company officials wouldn't reveal details on what products might result, they did say that their combined hardware and software could be used to protect Internet-connected devices -- from handhelds to automated teller machines to cars -- from growing cyberthreats in a consistent manner.
McAfee CEO Dave DeWalt wrote in a blog post that the "current cybersecurity model isn't extensible across the proliferating spectrum of devices…. The industry needed a paradigm shift, incremental improvements can't bridge the opportunity gap." Intel CEO Paul Otellini got more specific at the acquisition press conference: "We believe that security will be most effective when enabled in hardware."
The combination of companies – McAfee would operate as a subsidiary within Intel's Software and Services Group -- could also open up new sales opportunities. "Everywhere we sell a microprocessor, there's an opportunity for a security suite," Otellini said of what would be the biggest deal in Intel's history. Though he stressed that Intel is open to working with other security companies as well. (A short history of Intel acquisitions.)
While it's not immediately clear what impact the deal will have on corporate customers, industry watchers weren't shy about issuing warnings.
"It scares me," says Gartner research director Peter Firstbrook, who worries about whether the deal will distract the Santa Clara security company from efforts such as uniting its assorted security projects under the ePolicy Orchestrator management system. He also has concerns for customers with heterogeneous hardware environments that Intel and McAfee technologies might become too entwined to the exclusion of others.
However, Firstbrook does acknowledge that McAfee could bring Intel R&D that will improve its processors and provide hooks into its hardware that could be exploited by McAfee and other security vendors.
Forrester analyst Andrew Jaquith questions the whole premise of tying security so tightly to hardware. "Most enterprises take the least-common-denominator approach to managing their computing assets," he wrote in a blog post. "This is largely because refresh cycles cause hardware platforms to stick around much longer than software-based ones: it is easier to push down a software update than to pull a motherboard. I am not convinced that a hardware-based strategy for security will resonate with enterprise buyers. If you need convincing, ask yourself: how many of the PCs in your organization run Intel vPro-capable hardware? Don't know the answer? Right: this is exactly my point. Despite Intel's efforts to add more differentiating "professional" features on and around their core processor silicon, these are seen as a bonus, rather than the centerpiece of enterprise management strategies. It is hard to see how 'McAfee Inside' would work out any differently."
Allan Krans, senior analyst for Technology Business Research in Hampton, N.H., says the deal is not without challenges, but does think it could result in IT shops seeing a difference in how security is delivered.
"The prospect is clearly there to embed more security features right into the chipset, whereas now a lot resides above the hardware and even operating system level," he says. "Some of the security features customers currently pay separately for may be embedded in the hardware as a result of this acquisition."
Krans says the deal reminds him of EMC's RSA buyout in that EMC wound up "building in rather than bolting on security…[Buying McAfee] will enable Intel to streamline the delivery of more security functionality and also differentiate its hardware offerings in the market."
Intel-McAfee impact on software security market
The proposed buyout also raises many questions regarding the security software market, which Gartner expects will grow as much as 11.3% to $16.5 billion this year. McAfee – with about $2 billion in revenue last year and 6,100 employees – is currently the No.2 company in the market behind Symantec, but a hungry pack of vendors including Trend Micro, IBM, HP and Cisco is also fighting for its share, with HP earlier in the week snapping up software assurance company Fortify.
Krans notes that the deal would make Trend Micro the only true pure play security vendor among the biggest players, eliminating one of McAfee's current differentiators vs. Symantec, which also sells storage and systems management tools and has been in the process of better focusing its security offerings. (Interestingly, Intel sold its antivirus business to Symantec in 1998.)
Symantec holds just over 20% of the security software market worldwide, and while that's not bad, it's actually down from the 24.11% share it had in 2007 and the company recently warned of cautiousness among tech buyers. The company's stock price rose following the announcement of the Intel-McAfee deal, with speculation Symantec itself might be the next security company to find a suitor.
"The competitive landscape for us is changing," says Bill Robbins, Symantec executive vice president of worldwide sales, discussing the overall market prior to the Intel-McAfee announcement.
Symantec just spent many millions of dollars to buy PGP, GuardianEdge and VeriSign's authentication business to get encryption and certificate technologies. (Trend Micro will soon be unveiling some encryption-related plans as well.)
Such diversification isn't a bad idea, since selling security to the enterprise is increasingly a matter of having lots of different enticements to offer the customer--sometimes a giveaway in a bundled offering. "I've seen deals where the encryption is free," noted Gartner analyst Neil McDonald discussing the topic recently.
Though fellow Gartner analyst Firstbrook isn't quite sure how some of McAfee's products, including firewalls and secure Web and e-mail gateways, will fit into Intel's long-term plans. He also questions how the companies' cultures will mesh, describing Intel's as staid and McAfee's as more aggressive in that it is used to reacting quickly to the latest cyberthreat.
McAfee's big push of late has been security for smartphones, including the iPhone and Android-based devices, whether in the hands of the consumer or the business person.
To that end, McAfee recently acquired mobile-device management vendor Trust Digital, used in the enterprise, and Singapore-based tenCube in the consumer area. Symantec's approach so far has been to develop software in-house, including its Mobile Management product introduced last November, according to Khoi Nguyen, group product manager in Symantec's mobile security group.
McAfee's recent acquisitions are seen as being a good fit with Intel's visions of securing all Internet-connected devices -- the 5 billionth of which this month is expected to be plugged in, according to IMS Research. Those deals, and Intel's proposed buyout of McAfee, also would seem to fit with Intel's acquisition last summer of Wind River, a maker of embedded technologies used in mobile devices. Otellini says that the McAfee buyout supports Intel's contention that security, along with Internet connectivity and energy efficiency, are the three most important pillars of computing today.
IDG News Service contributed to this story.
http://www.macworld.co.uk/digitallifestyle/news/index.cfm?newsid=3236378
|
| Back to top |
|
|
| |
| An underground credit card clearing house has itself been hacked, an investigation by Trend Micro has confirmed. The operation - a holding firm for anonymous payment service Fethard - processes credit card payments for a rogue's gallery of fake anti-virus (scareware) suppliers, spam-promoted unlicensed pharmaceutical and extreme pornography sites.
Hackers claimed to have breached a server behind its website on 23 July, publishing information online including employee emails and recorded phone calls, one discussing techniques to defraud credit card firms. The perpetrators of the hack and their motive remain unidentified, but it is potentially an assault from cybercrime rivals.
Trend said the information on the unnamed credit card processor, registered in the Netherlands but actually run from Russia and Latvia, checks out. The firm has legitimate customers in Russia as well as rather more unscrupulous clients, reportedly taken on to keep the business afloat after it became the victim of cybercrime itself a few years ago.
"In 2007, a large sum of money was stolen from Fethard's funds. This has undoubtedly created problems for Fethard and has possibly pulled the mother company deeper into the cybercrime business," Trend Micro researcher Feike Hacquebord explains.
"This hacking incident would probably make a lot of cybercriminals nervous. Unfortunately, the incident also puts the personal data of legitimate customers and of many ordinary Russians at risk."
http://www.theregister.co.uk/2010/08/16/underground_credit_card_clearing_house_hacked/ |
| Back to top |
|
|
| |
| An underground credit card clearing house has been hacked, according to Trend Micro security researchers. Leaked data from the hack include employee emails and recorded phone calls. "A group of hackers recently published detailed information from an underground credit card company," writes Feike Hacquebord, an advanced Threats Researcher with Trend Micro. "On July 23, an anonymous group claimed to have compromised a server of an online credit card processor company. At that time, however, the extent of the compromise was unclear. Looking at the data that was published leads us to believe that the compromise is very plausible."
Some of the stolen recorded conversations include individuals speaking about ways to defraud credit card companies.
"This hacking incident would probably make a lot of cyber criminals nervous," Hacquebord writes. "Unfortunately, the incident also puts the personal data of legitimate customers and of many ordinary Russians at risk."
http://www.thenewnewinternet.com/2010/08/16/credit-card-clearing-house-hacked-says-security-researchers/
|
| Back to top |
|
|
| |
| Many cybercriminals are probably nervous after an unidentified group of hackers managed to compromise a credit card payment processor used in illegal operations and leaked detailed information about its customers. According to researchers from Trend Micro, who looked into the breach, the compromised company was known for having ties to the cybercriminal world.
It was regularly used for payment processing by FAKEAV schemes, pharma spam, unconventional adult-oriented websites, warez and other illegal operations.
However, the company also had legitimate customers, many of which of Russian nationality, who's details are now circulating on underground forums.
The hackers are even said to have lifted employee email and voice communications from a compromised server.
"A particular recorded conversation discussed the various ways of defrauding major credit card companies.
"Another conversation discussed Fethard, a payment service that allows anonymous payments to be made and that is often associated with money laundering and other cybercriminal activities," Feike Hacquebord, advanced threats researcher at Trend, notes.
One of Fethard's owners, which is suspected of having had strong ties with the crutop.nu underground forum, is also said to be one of the people behind the now compromised credit card processing company.
The firm is officially headquartered in Amsterdam, the Netherlands, but according to researchers only a handful of employees are actually based there, the bulk of the operation being handled in Russia and Latvia.
"This hacking incident would probably make a lot of cybercriminals nervous. Unfortunately, the incident also puts the personal data of legitimate customers and of many ordinary Russians at risk," the Trend Micro researcher, concludes.
Follow the editor on Twitter @lconstantin
http://news.softpedia.com/news/Cybercriminals-Uneasy-After-Underground-Payment-Processor-Breached-152286.shtml
|
| Back to top |
|
|
| |
| A group of hackers has published information about potentially illicit activities at an online credit card processor company. The anonymous crew claimed to have compromised a server of the unnamed credit card processing company, taking data from employee emails and recorded phone calls, according to Trend Micro's TrendLabs team. One recorded conversation discussed defrauding major credit card companies, while another mentioned Fethard - a payment service that has been associated with cyber crime activities such as money laundering.
It has also been suggested that the compromised company is the parent of Fethard, through which payments for fake anti-virus products and extreme pornography have been processed, the researchers said.
"There are assumptions that one of the people behind the credit card processor company also serves as one of the Fethard's owners," Feike Hacquebord, an advanced threat researcher at TrendLabs, reported in a blog post.
"In 2007, a large sum of money was stolen from Fethard's funds. This has undoubtedly created problems for Fethard and has possibly pulled the mother company deeper into the cyber crime business."
Despite the links to illicit activities, the company also carries out legitimate business, with official headquarters located in Amsterdam and a number of customers in Russia as well, Hacquebord said.
"This hacking incident would probably make a lot of cyber criminals nervous. Unfortunately, the incident also puts the personal data of legitimate customers and of many ordinary Russians at risk," Hacquebord added.
No motivation for the compromise has been forthcoming, although a rival gang could be behind the attack, or ethical hackers looking to make their mark.
http://www.itpro.co.uk/626113/hackers-hunt-hackers-in-credit-card-company-compromise |
| Back to top |
|
|
| |
| Online scammers are resourceful people who take advantage of people's gullibility and lack of knowledge about Internet dynamics, but once in a while they happen to stumble upon users who will know who they are dealing with and are willing to play along and lead them on a merry chase. Trend Micro researcher David Sancho is one of those. Admittedly, it's his job to do so, but it is nevertheless very nice to see an intended victim waste the spammers' time. He caught the fraudster's attention by putting up an advertisement on Facebook Marketplace, in which he professes his intention of selling his car. A few hours pass, and he is contacted by a woman named Caroline McMillan. She asks for further details, agrees on the price without even seeing the car and says she will be paying through PayPal.
Immediately, Sancho gets suspicious - why would anyone buy a car without seeing it first? And paying through PayPal? He does a quick online search, finds accounts of similar scams that convince him that he's talking to a scammer, and decides to have some fun and discover all he can about it.
He sends his PayPal address for the payment to be effectuated, and right away the scammer tips her (or his?) hand: she can't pay because she has to wire money to the collection agency to have the car picked up and says they don't accept credit cards, and asks Sancho help by transferring 750 euros via Western Union.
He, of course, refuses to part with any money until he gets the originally asked sum on his PayPal account, and he says so to the fraudster, who agrees to make the payment immediately.
Shortly after, Sancho gets two emails: one is purportedly from PayPal, and the other from an A. Williams, of "the PayPal Team". "Williams" says that the funds are in Sancho's account, and that they are waiting from his Western Union transaction confirmation in order to free up the money sent to him by "Caroline". Both emails are so poorly written that it's obvious they aren't legitimate.
The researcher says to the scammer: "I haven't received the money in my account yet. I'll notify you when I do." She replies by reiterating that he must sent the money through Western Union. "Kindly read the mail sent to you very well," she says, obviously referring to the fake PayPal email.
But Sancho has had enough. Knowing that he found out as much as he could in the circumstances, he decides to finish his correspondence with one last message containing a bit.ly link to a website that details this particular kind of scam. Shortly after, he checks the statistics for the link: a single hit from Nigeria, the world-famous haven for online scammers.
http://www.net-security.org/secworld.php?id=9766 |
| Back to top |
|
|
| |
| Other examples of positive evangelistic usage, based on our experiences with them, come from Sean-Paul Correll, who is with Panda Labs, and David Perry from Trend Micro. There are some bad examples as well, but we will avoid naming them here. They know who they are.
- - -
For some, when you think of evangelism, you imagine sales and thinly veiled product placements. For those used to dealing with evangelists, such as the media, there is far more to the position than sales. We recently got a chance to speak to HP's new security evangelist, Rafal Los, to talk about his new position and security evangelism as a whole.
At The Tech Herald, we have tapped Los for Web Application Security commentary on more than one occasion. The reason is simple; he offers information in easy to follow segments and is blunt in his delivery. While he is a known employee of HP, he always avoids pitching products to us when we ask him for information. To be honest, we have to actually mention HP before he will explain their take on things.
Still, there are plenty of misconceptions in the IT industry when it comes to evangelism. Most of this is due to the close ties that evangelists have to the sales and marketing teams within a company. At the same time, the bad reputation that some evangelists have is due to how they are utilized by their bosses.
Take for example Ryan Naraine and Dennis Fisher, who are Security Evangelists for Kaspersky Labs. They are respected reporters, and never once have they blatantly pitched Kaspersky, despite countless articles written between the two of them on anti-Malware related topics.
Other examples of positive evangelistic usage, based on our experiences with them, come from Sean-Paul Correll, who is with Panda Labs, and David Perry from Trend Micro. There are some bad examples as well, but we will avoid naming them here. They know who they are.
While in Las Vegas for BlackHat last month, we caught up with Los to talk with him about his new position. We asked about his initial thoughts when he was tasked with the job, as well as some of the drawbacks to his position and common misconceptions.
Overall, he was pleased and excited with the new position, but then again, he has been a vocal supporter of Web Application Security for years.
"There is a ton of opportunity, and I think I've got my work cut out for me. There's a lot of work to do, industry awareness, internal awareness, and just evangelism in general," Los said.
So what are the drawbacks to his new job?
"The biggest personal drawback is the travel and that it keeps me away from home and my routines. On a professional level, the responsibility of being an "evangelist" (essentially the public-facing entity for an entire organization's message) isn't simple either," he explained.
His role means that he has to mesh HP's business strategy and industry trends, all while balancing it "…against what really helps our customers succeed through a message that makes sense, and isn't perceived as pushing an agenda. That is certainly not trivial."
"Being an evangelist means breaking through the agenda-based forces that divide the security industry along vendor lines, create confusion for businesses, and act as a barrier to their success, and it's tough."
So is this selling out? Los doesn't see it that way at all.
"I think that this is the exact opposite of selling out. Selling out would be doing the everyday thing, right? Being the sales guy," he said. "This is something I'm passionate about, something we're [HP] passionate about, and to us it's a big deal."
Two of the most common misconceptions are that security evangelist is just another name for a sales role, used to further the HP agenda, as one person put it to him, and that a company as big as HP just won't take this seriously.
"Both couldn't be further from the truth," he said. "It's amazing how many people have already rushed to provide assistance, support, and opened doors internally and externally for me to get the message out. Frankly, I can't wait to prove the doubters wrong."
HP will give Los a lot of latitude to talk about what is relevant and what's important over what sells he told us. While HP sells Web Application security appliances and software, "it's more important to us, as an organization, that our customers and the industry realize that Web Application Security is a big deal."
The first thing he wants to tackle is breaking security out of the security silo.
"I know, it's been said before but no one's doing anything about it! We scan, test, and collect vulnerability metrics and no one cares outside the security organization. The risk level doesn't actually drop, yet we pat ourselves on the back as we fail the business. Becoming an integral part of the 'business of IT' is something security must learn to do, and it's more than just tools (products). It requires a level of thinking most organizations are afraid of."
To Los, this means that security must become a sub-topic of quality testing.
"Think about that. Overall software quality should have three components or three questions it answers: Does it work? Does it perform? Is it secure? If any of those three fail it's a loggable, traceable, reportable and fixable defect."
Essentially, Los told us, the process is one of Application Lifecycle Management, and security swallowing its pride and becoming a component of software quality "rather than trying to continue to fail on its own."
Los has blogged and spoken publically about security topics that range from Web Applications to common IT mistakes. This new role at HP is in reality positive recognition for the advice and insight he has offered to the community for years in an unofficial capacity.
It won't be easy. It will be a serious challenge, and that's something he lives for.
http://www.thetechherald.com/article.php/201033/6027/Insider-The-world-of-security-evangelism
|
| Back to top |
|
|
| |
| We've been using Housecall for years--it's Trend Micro's free, online malware-scanning tool. While other vendors provide free online virus scans, Trend Micro's, we've found, is among the fastest and most robust--and it's worked for us in the CRN Test Center for so long, it's long ago passed the threshold of trustworthy technology. The caveat is that a PC that's infected and can't access the Internet can't make use of this online scan (for obvious reasons) 
It's a nifty tool that even VARs can use when troubleshooting problem PCs. It's fast, it finds, cleans and isolates malware as quickly in Windows 7 as any other, and can really work to eliminate performance killers.
http://www.crn.com/slide-shows/applications-os/226700463/10-tools-to-speed-windows-7.htm;jsessionid=NjRyfm+kdo7Eh2jIGUA5NQ**.ecappj02?pgno=8
|
| Back to top |
|
|
| |
| Avnet (NYSE:AVT) has agreed to acquire itX Group, an Australian distributor for $69.2 million in cash. itX distributes software, hardware and services from vendors including IBM (NYSE:IBM), Hewlett-Packard (NYSE:HPQ), VMware, Apple (NSDQ:AAPL), Citrix (NSDQ:CTXS), Red Hat, and Trend Micro. The company generated about $131.5 million in sales for the fiscal year ended June 30 and has about 150 employees and six locations I Australia. In addition, itX also includes other specialty distribution divisions: Briell Marketing, which carries printers and media for personal identification and security cards, medical and photographic imaging; and Sydmed, a distributor of medical devices; and ICO, which provides IT hosting solutions.
"This acquisition is another step in our strategic expansion in the Asia Pacific region and, in particular, increases our scale and scope in the Australian market," said Phil Gallagher, president of Avnet Technology Solutions, Global, in a statement. "The itX business adds complementary suppliers and business partners, while doubling Avnet Technology Solutions' presence in Australia."
The acquisition is subject to approval of itX shareholders and Australian court approval.
Avnet shares were trading at $24.12, down 29 cents or 1 percent Friday afternoon.
http://www.crn.com/news/channel-programs/226700225/avnet-plans-to-buy-australian-distributor-itx.htm;jsessionid=WrbRbMr3CN6-+phPXQRolg**.ecappj01 |
| Back to top |
|
|
| |
| According to Trend Micro (a security firm), their researchers had noticed lots of suspicious files with a strange digital signature. While analyzing some samples of Zeus, Trend Micro discovered numerous other files with signature that appears to belong to another renowned security vendor, Kaspersky. The researchers at Trend Micro explained that the signature instantly grabbed their attention because that appeared to be signed by an authentic antivirus company called Kaspersky, as reported by The Tech Herald on August 5, 2010.
The researchers further explained that while they were examining the certificate, they observed that the hash value related to the suspect file was not valid. This was because the hash values were particular to the original file to which they were related but this specific signature had been stolen.
The signature exploited in this particular case seems to be stolen from Kaspersky's "ZbotKiller" cleaning tool. On further investigations, the security researchers found that the dubious files were certainly malicious -- ZeuS (ZBOT) variants, identified as TSPY_ZBOT.BWP, TROJ_ZBOT.BYM, and TROJ_ZBOT.KJT.
In addition, they disclosed that this wasn't the first incident when cyber criminals had stolen digital signatures. The first ever STUXNET malware was signed using a certificate from Semiconductors Corp. Another variant was later on signed with JMicron Technology.
Commenting on the issue, the security experts said that this seemed to be a fast emerging pattern among malware distributors and served as a good reminder to users, to always verify the details of signatures and to make sure that they were valid.
They further explained that unluckily certificates could be replicated by any cyber criminal with target from any firm. For instance - in this particular case, the company could not have avoided this incident from talking place, and it is possible to see many such confrontations in future.
Meanwhile, it is noted that the Zeus Trojan has been continuously in news for the past many days. In the first week of August 2010 alone, there have been two incidents and studies linked to Zeus (excluding the one mentioned above) that gained wide media attention, with each one highlighting the power of this malware and the harm it can cause. The security experts commented that the Zeus Trojan had been busy all this year (2010).
http://www.spamfighter.com/News-14935-Cyber-Criminals-Use-Zeus-Variants-To-Snatch-Certificates.htm |
| Back to top |
|
|
| |
| In its latest report on Internet security, Cyveillance Inc. a contractor for cyber intelligence based in Arlington (USA) states that conventional anti-virus software are still lagging behind cyber-criminals insofar as spotting as well as safeguarding against rapidly-evolving and fresh attacks from malware are concerned. The security company, for its study, experimented with 13 well-known anti-virus applications -McAfee, Symantec, Sophos, Trend Micro, F-Secure, Kaspersky, AVG, F-Prot, Dr. Web, Nod32, Norman, Virus Buster, and eTrust-Vet and found out their percentage of detection spanning 30-days. A database of about 1,708 files known to be malicious was utilized for finding out the lag and detection percentages of these anti-viruses.
The ensuing results showed that well-known AVs just detect a mean of 18.9% of fresh attacks from malware. By the time it's the 8th day, the mean detection rate becomes 45.7%. The rate increases to 56.6% on the 15th day, 60.3% on the 22nd day, and 61.7% after the 30th day.
Furthermore, the report states that the best of AV applications consume a mean of 11.6 days for coping up with fresh malicious programs. And as this doesn't cover those malware signatures that remain unidentified even after day 30, Internet-users seeking protection are advised not to depend solely on anti-virus solutions, according to Cyveillance.
Said COO Panos Anastassiadis of Cyveillance in one press release, even after a period spanning 30 days a lot of AV companies remained unable to spot known attacks. Consequently, enterprises were critically required to become more proactive towards securing the Internet so that the chances of infection could be lessened, he explained. The release was published on Cyveillance's website on August 4, 2010.
Anastassiadis continued that to enhance self-defense, users mustn't visit disreputable/unknown websites; should raise their Web-browsers' security configurations; and must ensure malware block charts' presence for enhancing personal devices' security. He added that only via reactive and proactive means was it possible to accomplish a strong safety ground.
Meanwhile, according to the Cyveillance researchers, since cyber-criminals manage to get past many security solutions by planting freshly designed malware therefore, users must deploy that security software which copes up with these malware adequately.
http://www.spamfighter.com/News-14933-Popular-AV-Solutions-Miss-Most-Malware.htm |
| Back to top |
|
|
| |
| Summer's fun and sun are waning, heralding the dark harbinger of fall and the back-to-school season.
It was sweet while it lasted, but now it's time to begin bracing for buckling down, including making sure students have the appropriate accoutrements. That usually includes a laptop, a mobile phone and perhaps some kind of digital music player. But there are other useful high-tech items to supplement these arguable essentials. Consider some of these gems to help round out any back-to-school gear up.
For the college-bound, that brand-new laptop will serve many needs for both education and entertainment until it walks off because someone left their dorm room door open, and no one was around to see the thief snag it. The ComboSaver combination portable notebook lock from Kensington can prevent such tragedies from unfolding, and for a fraction of the price of replacing a stolen laptop at $24.99. The Combo Saver's self-coiling cable extends from 3 inches to 6 feet, and its slim-profile lock attaches to 99% of notebooks, Kensington says. A combination lock means there is no key to be lost, and the system supports a possible 10, 000 codes. It's available at online and local retailers, including kensington.com and Office Depot.
Student schedules can vary drastically day to day, and the Neverlate 7-day alarm clock accommodates those differences by offering seven independent, programmable daily alarms. Students who like to stack classes on Mondays, Wednesdays and Fridays can set the Neverlate for a 6 a.m. wakeups but easily sleep in Tuesdays and Thursdays. Its sleep timer, nap timer and snooze duration can all be customized and a built-in radio promises awakening audio other than an obnoxious buzzer. The clock also has a battery backup of two AAAs in case the AC power goes out. Seriously, there is no longer any excuse for not getting up on time. It costs $34.99 at think geek.com and retailers found at americaninnovative.com.
The only reason students might have trouble getting up on time is because they've been up late studying, right? Blame - and praise - the LightWedge reading light, which serves double duty as a bookmark and a subtle source of illumination for students sharing space with others who might be sleeping. It's thin and light at 8.5 ounces, and the Light-Wedge's LED radiates 40 hours of glow through a clear acrylic lens. It comes in several sizes, including "paperback," which costs about $24.99 and "original" for about $34.99 at Borders bookstores and other retailers found at lightwedge.com.
Unfortunately, not all students will be considerate of their surroundings and neighbors. They'll blast their music and prattle on loudly while diligent, hardworking students are trying to focus on their studies. The QZ900 headphones from Koss can help block out yakking and yammering with both active and passive noise reduction technology. The electronics inside these headphones monitors outside noise through mounted microphones in each ear cup, analyzes it and generates a sound wave that is 180 degrees out of phase with the incoming signal. With background noise practically muted, the headphones transmit rich, clear sound with no distortion, helped by not having to jack the volume up to drown out surroundings. One standard AAA battery provides about 50 hours of active noise canceling. The QZ/900 costs between $250 to $140 at koss.com, buy.com and other online retailers.
The Koss headphones are so effective, students wearing them might not hear visitors knocking at their door. Thankfully those stopping by to say "hi" can leave a message on the Boogie Board LCD writing tablet affixed outside. This touch-sensitive LCD writing tablet is a high-tech whiteboard suitable for leaving messages and sketches.
The display lasts for about 50, 000 erasures, and it comes with a telescoping stainless steel stylus - although a finger will suffice in a pinch. The Boogie Board measures 8.8 inches long by 5.6 inches wide and provides about as much writing real estate as a half-sheet of letter-sized paper.
Artistic types can leave fancier doodles by varying the amount of pressure used when scrawling out lines, and the board can be blanked with the touch of a button. Its battery lasts six years assuming the tablet is erased 20 times a day. The Boogie Board costs $35.99 at retailers found at myboogieboard.com.
No student lair is complete without some kind of cooking implement, whether it's a microwave, hot plate or rice cooker. Granted, dorm rules vary depending on the school, but if it's campus-legal, consider the Max Burton 6000 Induction Cooktop. Measuring 14 inches wide by 12.6 inches deep by 2.5 high, this cooktop easily can be tucked away when not used. The device uses magnetic fields to generate temperatures from 140 to 450 degrees in iron or steel pots and pans. There is no open flame or blazing-hot heating element - you could even touch its surface while it is boiling a pot of pasta or sautéing a pan of veggies. Just don't touch the container that's on the cooktop. It's equipped with an LED display, 180-minute timer and overheat sensor.
It's available for $70 to $100 at online retailers like thinkgeek.com and amazon.com.
USB flash drives are common equipment for students because they're convenient for keeping documents close. Until those students forget them in a public computer lab, classroom or café. The LaCie CooKey USB flash drive is a solid metal USB flash drive shaped like a key and fits brilliantly on a keychain, making it a little harder to forget if it's left on the keyring while plugged into a computer. It's so it holds up to the abuse real keys suffer in a pocket or purse on a daily basis. These start at $19.99 for 4GB of storage and range up to $99 for 32GB, which should be more than enough for basic documents and casual photos. The CooKey is available at lacie.com, which also offers a list of other retailers.
Some students need more mobile storage than others, and that where Iomega's Skin eGo portable hard drives. These come in three bold designs - mostly black, mostly red or mostly silver - and offer monstrous storage of 500 GB. Yet measuring 4.88 inches by 3.35 inches by 0.69 inches, they take up little desk or backpack space, and at 0.36 pounds, are easily toted. The drives are self-powered, connect to a computer via USB 2.0 and compatible with Windows XP, Mac OS X 10.4 and beyond. Each comes with a suite of downloadable security software to protect the drive's contents that includes Trend Micro Internet Security and EMC Retrospect Express Backup software. They cost $119.99 at iomga.com, which also lists several online and national retailers.
The Pulse smartpen from Livescribe is a computerized ballpoint pen that captures pen strokes as you write and records the audio said while those notes were taken so when you tap any written word, you can hear what was said at the time. The smartpen takes notes like any other ballpoint pen, and, when it's turned on, a built-in infrared camera automatically absorbs everything written as long as you're using special Livescribe paper, which has a background of tiny dots. A starter notebook of 100 pages runs out quickly, and more substantial booklets start at $7.95. Visual captures of written notes and the audio taken in tandem can be uploaded to a Windows PC or Mac for long-term storage - transferred using an included cradle that also charges the pen. The Pulse pen costs $129.95 for the 2GB version, which can store about 200 hours of writing and audio depending on the recording quality. More advanced models with more storage are also available at livescribe.com, which hosts a list of addition retailers.
Some students will prefer a dumb pencil over a smart pen, and the Walking robot pencil sharpener will keep those pencils pointy. Open the robot's chest plate, insert a pencil and twist. That twisting winds up the robot, which sashays around afterward. It costs $5.99 at thinkgeek.com and amazon.com.
Students need a solid bag to carry their learning tools, and the Mamba Shift L from booq has loads of compartments and pockets to keep everything safe. In addition to accommodating a 17-inch laptop, there are several diagonally overlapping accessory pockets inside, a removable zippered pouch and elastic pop-out pockets built into shoulder straps. There are slip pockets for documents, a large pocket with a Velcro flap and a large mesh pocket, among others. The Mamba is made of water-resistant nylon on the outside and rip-stop lining on the inside to keep items dry and secure. It costs $149.95 or less at booq bags.com and various retailers found at the site's store locator.
.
Copyright 2010, Journal Sentinel Inc. All rights reserved. (Note: This notice does not apply to those news items already copyrighted and received through wire services or other media.) |
| Back to top |
|
|
| |
| I know cheap 1-terabyte hard drives are getting to be old hat these days, but you have to understand: I can remember when the PC reseller I once worked for was able to offer a 250-megabyte drive for $250, and what a big deal that was. I know cheap 1-terabyte hard drives are getting to be old hat these days, but you have to understand: I can remember when the PC reseller I once worked for was able to offer a 250-megabyte drive for $250, and what a big deal that was.
Consequently, when I see an Iomega Prestige 1TB USB hard drive for $59.99 shipped (after applying coupon code VN16W1W1JC2$MR at checkout), I can't not post it.
You'll be glad to know that this deal requires not two, not one, but zero mail-in rebates. What's more, unlike the Fantom drive that I usually find selling around this price point, the Iomega comes with backup software: EMC Retrospect HD. (You also get a one-year subscription to Trend Micro Internet Security, along with a couple of Iomega utilities.)
The drive features a USB 2.0 interface, an 8MB cache, and a very impressive three-year warranty. It comes with a desktop stand in case you want it to sit upright, monolith-style.
What more can I say? It's a terabyte of storage for $60 out the door. Kind of makes me wish I needed another hard drive.
By the way, the coupon code is good until August 21, but the drive could sell out before then.
Bonus deal: Who says you can't get something for nothing? Amazon Video on Demand is offering a free $10 credit with promotion code TVEMAILS. (Ignore the stuff about subscribing to the newsletter; it's not necessary.) I recommend "Breaking Bad" Season 1, which costs $10.99 (or $12.99 for the HD version). The code works only with the TV shows listed on the promo page (none of which are under $10, unfortunately).
Find more deals, coupon codes, and bargains on CNET's Shopper.com.
http://news.cnet.com/8301-13845_3-20013954-58.html |
| Back to top |
|
|
| |
| Security experts at Trend Micro have discovered that click fraud conducted through medium-sized botnet is a profitable business that can earn millions of dollars on an annual basis. Researchers at 'Trend Micro' have recently studied the click fraud cybercriminal model and stated that a medium-size botnet could earn hackers millions of dollars every year.
The company states that the networks used by these hackers can include more than 100 servers hosted at different data centers around the world. Some Internet groups have thousands of dollars in liquid assets which enable them to make considerable investments in latest criminal activities that ensure huge returns. Therefore, the collateral damage their activities cause is massive.
In order to explain their model, the firm took a specific botnet between March 2010 and the end of July 2010. The botnet's size changed frequently, it presently comprises of almost 150,000 bots. The firm stated that though this was not a massive botnet, but it was capable of generating thousands of dollars annually.
The firm informs that this botnet is comprised of systems infected with a special kind of Trojan called browser Hijacker. The computer Trojan downloads itself into the browser and takes user clicks to the sponsored search results on other websites that pay hackers for bringing traffic.
The technique is naturally more complicated and these landing sites are not essentially harmful. They are of legal advertisers who are generally deceived to accept the stream of bogus clicks, either by the alleged traffic brokers serving as facilitators or by the botnet runners directly.
The money per click that hackers earn is based on search keyword leading to clicked results. For instance, a click on a search result related to "facebook" (that gives nearly zero return on investment for advertisers) earns only $0.0072. On the other hand, a click on a result for "loans" or "home-based business opportunities" could earn nearly $2.
Finally, Trend Micro's report is supported by Click Forensics latest quarterly report. As per the report, cases of pay-per-click fraud in the online industry have considerably risen in the last few quarters as botnets and malware have become advanced. The firm discovered that average click fraud rate was 18.6%, up from 17.4% in the first three months of 2010 and 12.7% in the same months of 2009.
http://www.spamfighter.com/News-14956-Click-Fraud-Trojans-A-Profitable-Business.htm |
| Back to top |
|
|
| |
| It's no secret that anti-virus software doesn't do much to protect you against new and rapidly moving viruses, so it shouldn't come as much of a surprise that these suites don't do much good defending you against exploit code, either. A fresh evaluation from NSS Labs reveals just how vulnerable you really are. (Trend Micro) One of the reasons I've always taken interest in NSS Labs reports is because they are independently conducted and not funded by the security firms tested. In this report, NSS Labs tested the leading corporate anti-virus and end-point anti-virus applications on their ability to protect the host from exploit attacks. Exploit code is software that leverages application vulnerabilities to gain access. Many attacks today are in fact exploit-based attacks that are delivered in e-mail and malicious or compromised web sites and target web browsers, plug-ins, and client-side applications. These are the kinds of attacks that made the now famous Operation Aurora attack on Google and many other U.S. companies possible, and were heavily reported on earlier this year.
To conduct this test, NSS Labs took 123 common and already public exploits (many have been public for awhile, some years even) and tested them against a selection of the leading anti-virus vendors: AVG, Norman, ESET, Panda, F-Secure, Sophos, Kaspersky, Symantec, McAfee, and Trend Micro.
The results are dismal and, according to NSS Labs, reveal that about 75 percent of organizations are not adequately protected.
How unprotected?
Well, the average protection score was 76 percent against the original exploit and 58 percent for a similar or alternative exploit. Note these exploits were not obfuscated in any way, according to NSS Labs. So many attacks in the real-world would even be more successful.
In baseball, a 76% average would be outstanding. When protecting your data: not so much.
But when one looks beneath the averages the results are even worse. Only one vendor, the highest ranked, stopped all exploits thrown at it. The lowest ranked vendor didn't even manage to stop 70 percent of the exploits thrown at it.
Symantec, according to the report, only managed to stop 71 percent of the exploits thrown at it.
These just aren't acceptable results. So not only are software vendors not investing enough to develop applications that will keep your data safe, but neither are most of the vendors that purport to protect you.
For my security and technology observations throughout the day, find me on Twitter.
http://www.informationweek.com/blog/main/archives/2010/08/antivirus_suite.html |
| Back to top |
|
|
| |
| AV-Test this week published certification results for 19 software security products running on Windows 7. The test and consulting firm ranked the 19 antimalware products based on three categories: protection, repair and usability. Three products failed to get certified, including BullGuard Internet Security 9.0, McAfee Internet Security 2010 and Trend Micro Internet Security Pro 2010. The top performers (top scores in two of the three categories) were Kaspersky Internet Security 2010, Panda Internet Security 2010 and Symantec Norton Internet Security 2010. All passed with AV-Test certification, along with 10 other security products. The complete AV-Test list can be found here.
Microsoft Security Essentials 1.0, the free consumer antimalware solution, passed certification. According to AV-Test's MSE stat sheet, MSE had a top-ranking score on its usability tests. It also performed well in detecting widespread malware, but scored lower when protecting against zero-day malware attacks. It had respectable results cleaning malware off an infected computer. MSE also "achieved VB100 certification last week," according to a Microsoft spokesperson via e-mail. A Microsoft blog points to both achievements.
A Microsoft spokesperson attributed the positive usability results to MSE's lightweight design for consumers. It's designed to run on older PCs and only alerts users if an action needs to be performed. MSE is based on the Microsoft Forefront Client Security "engine technology, signatures and research teams," according to the spokesperson.
AV-Test conducted its tests during the second quarter of this year. For its protection tests, the firm examined the product's ability to deliver "static and dynamic malware protection" as well as protection against zero-day attacks, which leverage undisclosed vulnerabilities in software. Testing the repair capabilities involved checking product's "system disinfection and rootkit removal." In testing usability, AV-Test measured any system slow-down caused by the product, as well as any false-positive results.
Of six points total, products scoring lowest on the protection side included Norman Security Suite 8.0 (score 2) and Trend Micro Internet Security Pro 2010 (score 2.5). The sole low performer on the repair side was McAfee Internet Security 2010 (score 2). Results were a little more level on the usability side, with BullGuard Internet Security (score 3) achieving the lowest score.
Usability might seem to be the death knell for all antimalware products. According to a video by Kaspersky Lab, the amount of files requiring blacklisting by software security products has grown from 3 million files in 2007, to 17 million in 2008 and 34 million in 2009. The amount of malicious files has roughly tripled each year.
Kaspersky's software performed well on the usability side because of technology that handles old virus signatures, according to Roel Schouwenberg, senior anti-virus researcher at Kaspersky Lab Americas.
"If we were to uniquely identify each specific malware sample in our product, then, in a number of years, the size of the malware detection database would outgrow the average amount of RAM on the system," Schouwenberg said via e-mail. "However, new technologies allow us to create different kinds of signatures which can replace up to 100,000 old signatures."
Microsoft also uses technology to keep down the bloat of loading antivirus signatures.
"We're cognizant of file size and we try to streamline downloads and use generic signatures to target entire families of malware rather than release a signature for each variant," a Microsoft spokesperson said via e-mail. "We also revisit older signatures and tune them to catch current variants rather than create brand new signatures reducing the amount of accumulation of virus definitions and impact on system performance."
The option to use whitelisting isn't a solution to the potential bloat of antimalware solutions. A pure whitelist approach (using a slate of "good" executable files) would amount to more than 100 million files, according to the Kaspersky Lab video. Moreover, whitelists can get fooled. Schouwenberg pointed to cases where legitimate software gets loaded with malicious code, such as via the Induc virus.
"There are tons and tons of (digitally signed) files out there which have this [Induc] virus," he said. "Whitelisting can't be applied in a generic way and there are too many ways to basically fool whitelisting. For those reasons I'm convinced that we need to look at whitelisting mostly so that we can treat the non-whitelisted files with more suspicion."
The Kaspersky Lab video also suggested that cloud computing could be enlisted to better enable such a whitelist strategy.
About the Author
Kurt Mackie is online news editor, Enterprise Group, at 1105 Media Inc.
http://redmondmag.com/articles/2010/08/18/av-test-certifies-security-products-on-windows-7.aspx |
| Back to top |
|
|
| |
| Researchers at security firm Trend Micro have detected a phony MSRT (Malicious Software Removal Tool), which displays the real icon belonging to the original application. State the researchers that the phony MSRT proliferates online by penetrating PCs via system vulnerabilities. Often, it infects users when they access a malevolent website.
State the reports that the phony application has been designed so that PC operators can be cheated and persuaded into buying bogus AV software. This is how it happens. Immediately when the phony MSRT is installed, it pops up a dialog box impersonating the Windows update, while giving an impression that the Windows MSRT is being loaded.
Thereafter, there appears a scan supposedly with the help of Microsoft software that announces several infections. These infections appear listed in the dialog box along with a message stating that it hasn't been possible to remove all the listed infections.
Subsequently, users are directed that they must hit on the "Next" button and get the list of recommended AV products. Now these products include the Panda Antivirus and ESET NOD32, which are the only authentic anti-virus programs; however, as per the phony MSRT, these can't eliminate the malware infections.
Another product that the dialog box shows and also suggests that users buy it is named Shield EC Antivirus. Actually, this anti-virus program is a scareware, which only exhibits bogus security alerts and messages.
The security researchers while remarking about this stated that one could easily observe how the current scam technique might dupe a PC user having low experience. However, for those with more experience, there is a pair of extremely obvious warning signs. These signs are: first, the fake MSRT isn't digitally signed and secondly, the size of the file is utterly small (412,672 Bytes).
Here it's worth noting that the original MSRT doesn't randomly appear exhibiting notifications and alerts. Thus, the scammers utilizing their cunningly-designed MSRT hope and even have some users feel interested and buy it.
Stated the specialists, anytime users stumble on similar software they must cross-check it with software that's reliable. If spotted as dubious, they must remove it fast.
http://www.spamfighter.com/News-14972-Fake-Windows-MSRT-Utilized-For-Spreading-Scareware.htm |
| Back to top |
|
|
| |
| Posted in Soccer News, Sports - The August 19th, 2010 match between Liverpool and Trabzonspor is currently underway, and is set to be a great match-up. Liverpool is currently without Javier Mascherano and Daniel Agger, due to injuries. Manchelivarse.com reports that Fernando Torres could make his first start today. As for a live stream of the game, our news team has been searching for a stream that actually works. We found that the best stream of the game can be found at channelsurfing.net/watch-uefa-24.html. The stream does have some lag, but Trend Micro did not find any viruses in the stream, on our computer. Remember, this is a third party website. News by the People will not be held responsible for any of the content on the website. (UPDATE) The stream seems to be having some major issues. Unless they air commercials over the stream, the futbol game is currently not being shown. We'll keep you updated. UPDATE: We have looked to see if any other streams were available for this game and we ran into some viruses. Be careful!
If your computer cannot run the live stream or the live stream fails to work, you can get text-written live updates at Guardian.co.uk. Be sure to check out their article at Liverpool v Trabzonspor – live! Currently, the score of the game is Liverpool 1, Trabzonspor 0.
http://www.newsbythepeople.com/2010/08/19/liverpool-vs-trabzonspor-live-stream/ |
| Back to top |
|
|
| |
| It's unfortunate, but some marketeers thrive on perpetuating Fear, Uncertainty, and Doubt. One timely example, Trend Micro's recent news release titled "ATMs - Can You Bank on Their Safety?". Referring to a demonstration at the August 2010 Black Hat conference, the article proclaims, "One attack required a few seconds for the cybercriminal to open the ATM and insert a USB drive with a code to overwrite its system." Sounds scary, right? Only problem with that story is the demonstrator (Barnaby Jack of IOACtive) was using ATM machines he had purchased online. As in, he had direct physical access.
So when was the last time you saw a bank ATM that was not encased in steel-reinforced concrete?
http://antivirus.about.com/b/2010/08/20/depositing-security-fud.htm
|
| Back to top |
|
|
| |
| Tech 2.0 Extra: The new "Starcraft" game dominated software sales in the past month. "PC Starcraft II: Wings of Liberty" is the top-selling software for July, according to NPD Group. "Kaspersky Antivirus 2010," "Webroot AntiVirus w/Spy Sweeper 2010" and "Trend Micro AntiVirus 2010 Plus Anti-Spyware" bump down one place each to numbers two, three and four. "MS Office 2010 Home & Student 3User" is in fifth place, followed by "PC Starcraft II: Wings of Liberty Collector's Ed." In seventh is "MS Office 2010 Home & Student Product Key Card." "Norton 360 4.0 3User" is number eight, "iWork 2009" is ninth and "MobileMe" is number ten.
http://www.kpvi.com/story.php?id=25656&n=15207 |
| Back to top |






沒有留言:
張貼留言